| Assessment Type |
Coursework 2 |
| Assessment Title |
Report |
| Academic Year |
2024-25 |
| Submission date: |
July 16, 2025, at 11:59 PM. |
COMP11079 Overview of the Coursework
This coursework consists of two parts:
In Part A, you will analyse a suspect’s laptop image to trace any malicious activities performed by the suspect. You are required to create a soft copy of your logbook (PDF), a detailed forensic report (PDF). You can follow the template provided in the exemplar logbook accompanying this coursework to create your logbook.
In Part B, you will analyse a suspect drone images to trace forensic data. You are required to create a forensic report (PDF) based on various investigation questions provided to you.
COMP11079 PART - A
For this task, you will be given a digital image. Failure to use this image will result in a zero for the entire coursework. You are not allowed to change the image.
Your task is to complete and write a Digital Forensics Examiner’s report document, as detailed in section 3, and describe your process (with ample screenshots) that addresses the following case scenario:
- Your Role: Digital Forensics Examiner
- Request for Digital Forensic Analysis of Suspect Laptop
- Suspect: Mantooth, Wes
- Seizure Date: 25 October 2024
- Case Number: 001548
- Requesting Organisation: Cyber Innovation Lab @UWS
- Report to: Dr Manesh Thankappan
1. Requirements
Students must use various tools to analyse and identify artefacts of interest in each forensic image and other evidence related to the suspect or suspects, the type of crime (there can be multiple crimes), and the relationship between the evidence and the suspects.
2. Report Structure:
2.1. Logbook This report is worth 20/100 marks and must describe in detail the steps taken to collect and analyse the forensic image provided. You should describe how each step was performed, including examples of alternative forensic practice.
- In your logbook, you should list each of your taken tasks, start, end (date & time), finding, task description, and total hours spent each time he/she on the case. Use the logbook template available in assessment page.
- Mark Distribution: Using the logbook, answer 20 investigation questions given in Section 4, each carry 1 Mark→20Marks
2.2. Report The forensic report of your findings covers another 40/100 marks and is evaluated based on components that are correctly identified and discovered. Use the Report Template available in assessment page. Your main report must cover the following sections:
- Executive Summary: This section can contain background of the case and case number with overview of contents of disk images presented to you.
- Investigation & Findings: You are required to answer 20 investigation questions with detailed explanations. Each response should include a clear description of how the evidence was collected (with screenshots) and must effectively link the evidence to the suspected criminal activities, supporting your conclusions with relevant findings.
- Summary of Evidences: Include an overall discussion of the main findings (different types of crimes), limitations and implications, and detail the next steps (i.e., what else would you do if you had more time or have more evidences in proving the crime).
- Conclusion: Conclude overall investigation process
- Mark Distribution: Executive Summary (10 Marks), Investigation and Findings(20 Marks), Summary of evidences and conclusions (10 Marks)
2.3. Overall presentation and efforts done by student
This plays a crucial role in evaluating your overall effort in preparing both the logbook and the final report. It will be worth 10/100 marks.
3. Task Hints:
3.1. Tools to use:
- Autopsy
- FTK Imager
- Regedit
- Registry Viewer
- Email Viewer, EMOX Viewer.
- Communication Viewer
- NetAnalysis
- Or any other tools you might need to use on your investigation.
(Take screenshots of the output and process of the tools and use them in you reports)
3.2. Tasks: (for example)
- You may need to identify tasks to organise, perform, and review the case (this is just an example of the tasks that will help you investigate the case in order and prioritise your investigation → chain of the documentation; you may do this in different ways – depending on your investigation).
- You should take screenshots (as evidence and proof of your result) of the result of each task.
Task A:
- Download the “Coursework.e01” file from the Assessment Page
- Download and install Autopsy (if you haven’t already).
- Open a new case in Autopsy.
- Add the image data file Coursework.e01.
- Autopsy processes the image file as a source of evidence (this may take a few minutes)
- So, let's start your investigation using autopsy. For example, finding registry hives to answer the question in Part 4.
Task B:
- Track USB serial number …
Task C:
Task D:
Task E:
Task F:
- Registry analysis with Registry Viewer …
The Windows Registry provides valuable information about the system, devices, users, user activities, system behaviour, and more. Now you will work to select and extract the most useful elements for our analysis purposes.
- You can download access data, registry viewer from Assessment Page. You can also use any other tools you are familiar with.
- After installation, you can run the program and a window with the following warning will appear:
- Click No and run Registry Viewer in demo mode.
- In the new window that opens, click OK, and finally you will access the tool's user interface.
- In this task, you will need to export registry hives from Autopsy in Task A.
Export the following registry hives:
- SYSTEM
- SOFTWARE
- SECURITY
- NTUSER.DAT
Task F:
- The SAM hive can provide interesting statistical information about local users and device usage. For example, to see how many accounts are recorded, we can move to the SAM\Domain\Account\Users and count the subkeys present. Each subkey represents a user; its name is formed by four zeros followed by a hexadecimal.
Task H:
- Look into the installed application to collect as much data.
Task G:
- Registry analysis with Registry Viewer
- Extract the Windows registry with FTK Imager or Regedit.
4. Investigation Questions →
The below are the questions which you need to investigate it → You must analyse a case and answer them.
You must answer the following questions,
- What is an image hash? Does the acquisition and verification hash match?
- What operating system was used on the computer?
- When was the installation date?
- Who is the registered owner?
- What is the computer account name?
- When was the last recorded computer shutdown date/time?
- How many accounts are registered (total number)?
- What is the name of the user account that uses the computer the most?
- Who was the last user who entered the computer?
- Find installed programs that may be used for criminal activity (e.g. hacking, phishing, unauthorized access or etc.).
- Which email is used by Wes Mantooth and others?
- What websites was the Wes Mantooth accessing?
- How many executables files were used? And are these files really deleted? Or files are there in the recycle bin?
- How many files are reported to be deleted by the file system?
- Is encryption software installed on the Coursework computer?
- What is the most visited internet domain and how many times it has been visited?
- A search for the name of “Wes Mantooth” reveals multiple hits. One of these proves that Wes Mantooth is the administrator of this computer. What file is it?
- Which registry key holds the list of URLs the currently logged-on user typed into Internet Explorer?
- Which registry key would you use to discover the SID associated with a particular user?
- Which registry hives hold information about installed applications, and settings; along with information about any hardware that has ever been connected to the computer, including the type of bus, the total size of available memory, a list of currently loaded device drivers, and information about Windows?
PART - B
As a digital forensic investigator, you have been assigned a sensitive case involving unauthorized drone activity in a restricted area. Forensic images have been captured from the suspect drone.
Your task is to perform a detailed forensic analysis on the extracted dataset using your Kali Linux VM (or any other tools such as Autopsy or FTK Imager).
- Your Role: Digital Forensics Examiner
- Request for Digital Forensic Analysis of Drone Image
- Suspect: John Smith
- Seizure Date: 20 April 2018
- Case Number: 001648
- Requesting Organisation: Cyber Innovation Lab @UWS
- Report to: Dr Manesh Thankappan
1. Requirements
The objective of your investigation is to analyse logs, metadata, video cache, and captured images to establish facts regarding the drone’s operation and to identify key attributes about the unauthorized flight.
2. Instructions and Report Structure
1. Download and unzip the provided drone logical image “Android_Logical.zip” from the Assessment Page. Use Kali VM to trace the forensic data from the drone image and try to find out answer for Investigation questions from 1-10 in Section 3.
2. Download MicroSD card binary image “Drone_MicroSD.001” of same drone controller and use Autopsy or FTK Imager to trace out the videos or images captured by the drone and try to answer the Investigation questions from 10-12 in Section 3.
3. After forensic analysis, create a forensic report (single PDF) by with answers for the following questions along with supporting evidence (screenshots and explanations). This report will be worth 30/100 marks.
4. Mark Distribution:
- 12 Investigation Questions, each 2 marks →24 Marks
- Styling and clarity of report→6 Marks
3. Investigation Questions → The below are the questions which you need to
investigate it → You must analyse a case and answer them.
- What is the make and UUID of the drone?
- Where did the unauthorized drone flight occur? Identify GPS coordinates and describe the location.
- What was the take-off and landing date and time of the flight?
- What was the total duration of the drone flight?
- Reconstruct the complete flight path. (Use PhantomHelp or AirData as necessary)
- What was the maximum speed achieved by the drone during flight?
- What was the maximum altitude reached by the drone?
- What were the atmospheric conditions during the flight (temperature, humidity, wind speed)?
- Recover the actual drone footage from the forensic image. Record the file path, format of the video, bitrate, and total size.
- Recover all images or pictures captured by the drone. Record the timestamp and size of each image file.
- How many images and videos cab be traced from the MicroSD card of Drone controller? Show proper evidence from where (location) it is traced?
- How many people were shown or identified from the videos. Show their images (if possible their faces) with possible image quality.
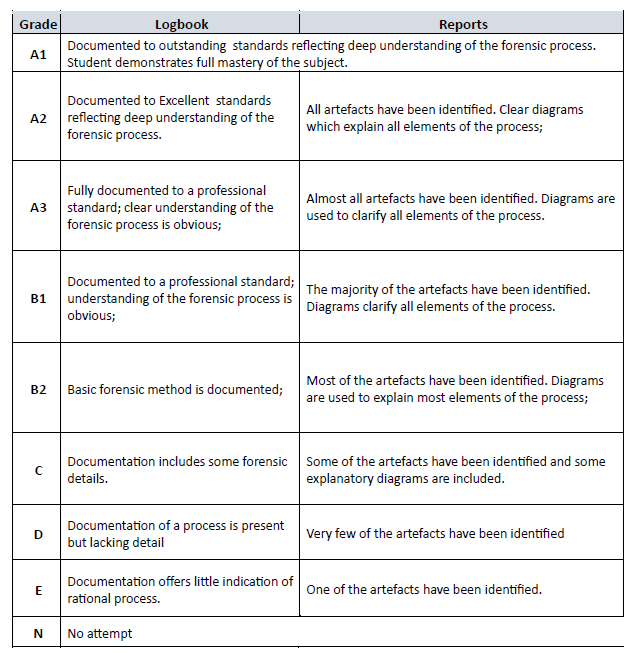
COMP11079 Marking Scheme
The table below outlines how the marks will be allocated by reference to the module marks and the university’s grading scheme.