| Category | Assignment | Subject | Computer Science |
|---|---|---|---|
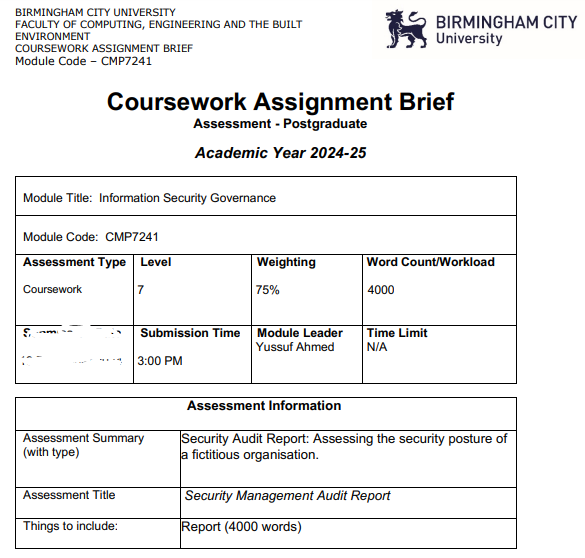
| University | Birmingham City University (BCU) | Module Title | CMP7241 Information Security Governance |
Completion of this assessment will address the following learning outcomes:
Present any written aspects of the assessment using font size 11 and using 1.5 spacing to allow for comments and annotations to be added by the markers.
Complete the appropriate cover sheet for this assessment and append your work.
This assessment will be marked anonymously and should show your student number only. Submit this coursework assessment task via Moodle.
Assessments must be submitted in the format specified in the assessment task, by the deadline and to the submission point published on Moodle. Failure to submit by the published deadline will result in penalties which are set out in Section 6 of the Academic Regulations, available at: https://icity.bcu.ac.uk/Quality-Enhancement-and-Inclusion/Quality-Assurance-and- Enhancement/Academic-Regulations
The maximum word count for this module assessment is shown on Page 1. A +10% margin of tolerance is applied, beyond which nothing further will be marked. Marks cannot be awarded for any learning outcomes addressed outside the word count.
The word count refers to everything in the main body of the text (including headings, tables, citations, quotes, lists etc.). Everything before (i.e. abstract, acknowledgements, contents, executive summaries etc.) and after (i.e. references, bibliographies, appendices etc) is not included in the word count limit.
Academic integrity is the attitude of approaching your academic work honestly, by completing and submitting your own original work, attributing and acknowledging your sources when necessary.
Understanding good academic practice in written and oral work is a key element of academic integrity. It is a positive aspect of joining an academic community, showing familiarity with and acknowledging sources of evidence. The skills you require at higher education may differ from those learned elsewhere such as school or college.
You will be required to follow specific academic conventions which include acknowledging the work of others through appropriate referencing and citation as explicitly as possible. If you include ideas or quotations that have not been appropriately acknowledged, this may be seen as plagiarism which is a form of academic misconduct. If you require support around referencing, please contact the Centre for Academic Success
It is important to recognise that seeking out learning around academic integrity will help reduce the risk of misconduct in your work. Skills such as paraphrasing, referencing and citation are integral to acting with integrity and you can develop and advance these key academic skills through the Centre for Academic Success (CAS).
To learn more about academic integrity and its importance at university, you can access CAS resources on Moodle. Furthermore, you can book on to workshops and request 1-2-1 support around key academic skills.
Style: Report
Rationale: Assess the student’s ability to perform a security audit using industry best practices.
Description: This assignment aims to perform a security audit on a fictitious company. The scenario is as follows:
CyberSafe is a large IT services company that provides cloud solutions and IT consultancy to clients in North America, Europe, the Middle East, and Africa. The company handle extensive client data, which makes cybersecurity a high priority for them, given the current threat landscape. Their IT infrastructure consists of Data Centres, Network Infrastructure, Servers, End User Devices, Software and Applications. This audit aims to assess Cybersafe's current security posture, identify vulnerabilities, and recommend ways to enhance the organisation's cyber defence capabilities. You will perform risk assessments, determine conformance against the ISO 27001 standard, and propose recommendations. You will also evaluate the company's cyber readiness and help them construct contingency and business continuity plans.
Knowledge of industry standards and their implementation
Order Custom Answers for CMP7241 CWK Assignment
Request to Buy Answer|
Marking Criteria:
Table of Assessment Criteria and Associated Grading Criteria |
|||||||
|
|
Marking Criteria:
Table of Assessment Criteria and Associated Grading Criteria |
|
|||||
|
|
Learning Outcomes |
1 Identify security threats and evaluate associated risks to information assets using appropriate quantitative and qualitative methods. |
2
Critically evaluate the conformance of security management processes of an organisation against ISO 27001, identify gaps and recommend mitigations. |
3
Construct contingency and business continuity plans that are consistent with the organization’s view of associated business risks. |
|
||
|
Assessment Criteria à |
LO1 |
L02 |
L03 |
||||
|
Weighting: |
25% |
25% |
25% |
||||
|
Grading Criteria 0 – 20% Fail |
No attempt was made to identify the threats and evaluate the risks and most of the information is out of context |
No attempt was made to evaluate the conformance of security management processes against ISO 27001 standards. No gaps were identified. |
No attempt was made to evaluate the contingency and business continuity plans. |
||||
|
20 – 39% Fail |
A minimal attempt was made to identify the threats and evaluate the risks. A substantial mismatch exists between the suggested controls and the proposed risks. |
A minimal attempt was made to evaluate the conformance of security management processes against the ISO 27001 standard. No clear gaps were identified, and the countermeasures were either non-existent or out of place. A Statement of Applicability (SOA) was not produced. |
Minimal evidence of contingency planning and business continuity plans. Key features such as business impact analysis are missing. Overall, there are lots of inconsistencies. |
||||
|
|
|
40 – 49% |
Limited evaluation of the threats and associated risks to the assets. Some mismatch between the gaps and the countermeasures |
Limited attempt was made to evaluate the conformance of the security management processes of the organisation against ISO 27001. The identified gaps and countermeasures were not sufficiently developed and linked to the risk assessment performed in the criterion. The Statement of Applicability was not clearly defined. |
Limited evidence of contingency planning and business continuity plans. Key features such as business impact analysis are missing. Overall, there are lots of inconsistencies. |
|
|
|
50 – 59% |
Satisfactory evaluation of the security threats and the associated risks to the assets using appropriate methods |
Satisfactory evaluation of the conformance of the security management processes against the ISO 27001 standard. Appropriate countermeasures were recommended to mitigate the risks. A Statement of Applicability was produced to justify the controls selection. |
Satisfactory contingency and business continuity plans. Key features such as business impact analysis and recovery strategies were described. |
||||
|
60 – 64% |
Competent evaluation of the threats and the associated risks using appropriate methods. |
A competent evaluation of the conformance of the security management processes against the ISO 27001 standard. Appropriate countermeasures were recommended to mitigate the risks. A good Statement of Applicability (SOA) was produced to justify the control's selection. |
A competent contingency and business continuity plan were constructed. The business impact analysis was performed, and key recovery strategies were covered in detail. |
||||
|
65 – 69% |
Good evaluation of the threats and the associated risks using appropriate methods |
A good evaluation of the conformance of the security management processes against the ISO 27001 standard. Appropriate countermeasures were recommended to mitigate the risks. A good Statement of Applicability (SOA) was produced to justify the control's selection |
A detailed contingency and business continuity plan was constructed. The business impact analysis was performed, and key recovery strategies were covered in detail. |
|
|
|
70 – 79% |
A very good evaluation of the threats, associated risks and potential impact using appropriate methods. Threats were ranked according to their severity and impact. |
A very good evaluation of the conformance of the security management processes against the ISO 27001 standard. Appropriate countermeasures were recommended to mitigate the risks. A clear and detailed Statement of Applicability was produced to justify the control selection. |
A very good contingency and business continuity plan was crafted. An in-depth Business impact analysis was performed to identify time- sensitive and critical business functions. Well-defined recovery strategies were created. |
|
|
|
80 – 89% |
Excellent evaluation of the threats, associated risks and their potential impact. A clear strategy to prioritise higher risks. Use of appropriate tools such as risk registers and risk analysis methods. |
Excellent evaluation of the conformance of the security management processes against the ISO 27001 standard. There was evidence of high-level risk analysis. Appropriate countermeasures were recommended to mitigate the risks. An excellent Statement of Applicability (SOA) was produced. The SOA contained the justification for selecting the controls and whether they were implemented or not. |
An excellent and effective business continuity plan was constructed. A well-planned and detailed business impact analysis was performed to identify all critical functions and processes. Metrics such as Recovery Point Objectives and Recovery Time Objectives were used and discussed in detail. |
||||
|
90 – 100% |
Outstanding report. The student used innovative techniques to evaluate the threats, associated risks and their potential impact. A clear strategy to prioritise higher risks. A high-level use of appropriate tools, such as risk registers and risk analysis method |
Outstanding evaluation of the conformance of the security management processes against the ISO 27001 standard. There was evidence of high-level risk analysis. Appropriate countermeasures were recommended to mitigate the risks. An outstanding Statement of Applicability (SOA) was produced. The SOA contained the justification for selecting the controls, why others were omitted, and whether they were implemented. |
Outstanding and highly innovative and effective business continuity plan was constructed. A comprehensive business impact analysis was performed to identify all critical functions and processes. Metrics such as Recovery Point Objectives and Recovery Time Objectives were used and covered in detail. |
||||
|
|
|||||||
Format: upload to the submission link on the Moodle page
Late Penalties
If you submit an assessment late at the first attempt, then you will be subject to one of the following penalties:
Please note:
Run through this simple tick list before submitting your work!
Well prepared materials make your work look more professional and easier to understand.
|
Item |
Action |
Done? |
|
1 |
I have used the spellchecker and proofread the work correcting errors several times. |
|
|
2 |
I have checked that all material is directly related to the assignment tasks. |
|
|
3 |
I have checked that all the required information has been included in the work. |
|
|
4 |
The work is professionally presented using consistent headings, fonts and layout. |
|
|
5 |
All tables and images are numbered and captioned. |
|
|
6 |
I have used the structure specified in the assignment. |
|
Your work will be subjected to checks to ensure it is not copied. Derivative work may leave you subject to penalties, including in extreme cases, expulsion from the University.
|
Item |
Action |
Done? |
|
1 |
All images and tables are fully referenced. |
|
|
2 |
I have not copied any material from anywhere else. All sentences have been paraphrased into my own words. |
|
|
3 |
All references appear in the references section at the end of the presentation. |
|
|
4 |
All references are cited in the text in the form of (author, year). See https://www.bcu.ac.uk/library/services-and- support/referencing for more details. |
|
|
5 |
If I have used quotes, these are fully referenced, appear in quotation marks and form only a small part of my work. |
|
Is your work complete? Have you included all the required elements?
Is your work complete? Have you included all the required elements?
|
Item |
Action |
Done? |
|
1 |
I have created the asset register, identified the threat and vulnerabilities and overall risks. |
|
|
2 |
I have chosen the 15 assets with the highest ranking and calculated the overall risk |
|
|
3 |
I have evaluated the conformance of security management processes against the ISO 27001, recommended mitigating controls and provided a statement of applicability. |
|
|
4 |
I have completed the business continuity plan including the business impact analysis |
|
|
5 |
I have completed all the tasks and uploaded the report to Moodle |
|
Buy Custom Answer Of CMP7241 CWK Assignment & Raise Your Grades
Get A Free QuoteLooking for the solution of the CMP7241 Information Security Governance CWK Assignment? Look no further! There are specialized professionals for all categories of assignments who offer you plagiarism-free and superior content. You are assured that our computer science assignment help service will make you productive and help you achieve high grades in your academic year. A free list of BCU Assignment Samples written by PhD experts is also provided here that can help you boost your study power and check the quality of the assignment. So contact us today and get your top-notch assignment!
Hire Assignment Helper Today!
Let's Book Your Work with Our Expert and Get High-Quality Content
