| Category | Assignment | Subject | Computer Science |
|---|---|---|---|
| University | University of Derby (UOD) | Module Title | 7CS093 Securing Networks |
| Assessment Type: | Group Presentations and Report (group work, up to 5 students) |
| Assessment weighting: | 100%-Portfolio Presentation 1 contributes 20%, Presentation 2 contributes 20% and the final Report contributes the remaining 60%. |
| Word count/Length : | Presentation (10 minutes) and maximum word count for the Report is 4000 words, including all images, tables, charts, and references. |

You are required to design and protect a network from external and internal threats and discuss different methods of system breach. Apply or amend the taught techniques to provide mechanisms necessary for detecting and protecting against them, e.g., Firewalls, Anti-malware and Intrusion Detection, and Prevention Systems (IDPS). You will be assessed on your ability to demonstrate your ability to design a network and an understanding of how the attacks can be detected, and how mitigation techniques can be applied.
You have just joined a company ABC as security analysist and IoT architect. The first project you have been tasked with is the setup of a demo IoT Smart Office, with a link to the company offices. The project is divided into 3 parts:
The Main Smart Office includes, but is not limited to the following smart devices:
These devices are linked to a Wireless Router, which is linked via an Ethernet cable to a Cable Modem. The modem is connected to the Internet via an ISP. All the devices registered on the Remote Server can be controlled locally by a Tablet which is also connected to the wireless network. There is a Remote Server connected to the Company's Cloud Cluster service, as well as an external server that the Smart office uses for backups. Ensure that you add all necessary screenshots with the documentation and submit your packet tracer file along with the report on Turnitin.
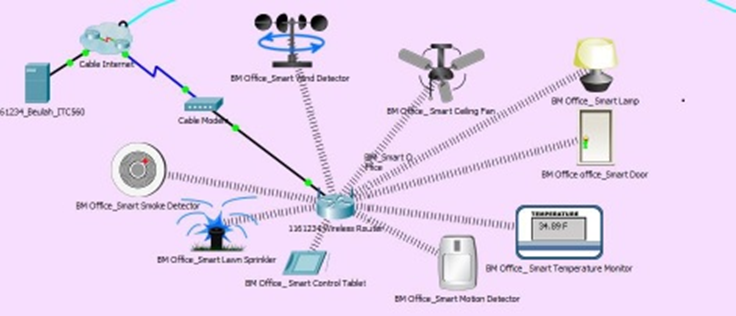
Figure 1: Smart devices interconnection
Do You Need Assignment of 7CS093 Presentations and Report
Order Non Plagiarized AssignmentAdd a new branch office in the same city. Either move the same tablet to the branch office or use your smart phone and connect to the main smart office server. You can use any connecting and intermediary devices of your choice. Log on to the web browser on your tablet/smart phone and manage the devices.
Use your tablet/smart phone to:
Step 3: Assess the network and protect it from external and internal threats and discuss different methods of system breach. Apply or amend the taught techniques to provide mechanisms necessary for detecting and protecting against them. You can use the following tools and equipment:
Also discusses any other conceptual techniques and approaches that can be used to detect attacks and explain mitigation techniques to secure the SmartOffice.
This portfolio assignment has THREE components, you must attempt all three components. If the implication of this is unclear, please ask!
In this part of the assignment, you are required to prepare and deliver a PowerPoint presentation that clearly defines and explains the concepts and components of a Smart office. You should consider every possibility of the environment / devices that could be controlled or monitored. You should identify how devices will co-exist on the network. You should include detail of the control / monitoring process and procedure and include details of how the controlled / monitored and controlling / monitoring / reporting components communicate.
This part of the assignment, you are required to prepare and deliver a PowerPoint presentation that clearly defines and explains the vulnerabilities of the Smart office network defined in presentation 1. You should include direct and indirect vulnerability concepts as well as remote, local, and physical attack vectors. You should include potential / conceptual as well as reported vulnerabilities and present various mitigation techniques.
The final part of the assignment is to construct a well written report which
At this level, it should be very clear that none of these stages are optional. For absolute clarity: in addition to scoring zero for the component, your final mark will be reduced by 20% for each missed component. Submit your packet tracer file along with the report on Turnitin, it is worth noticing that only submitting a packet tracer file while not submitting the report may result in a grade "FAIL". The report must have all the scenarios, results, and investigations. It is intended that the presentations will be held in the normal practical / tutorial period however you may be expected to attend outside of this period to make your presentation. This is to ensure that everyone has adequate time to present and be given feedback.
Buy Answer of 7CS093 Presentations and Report & Raise Your Grades
Order Non Plagiarized AssignmentAre you a University of Derby student and facing problems with your 7CS093 Securing Networks Group Presentations and Report Assignment? Don't worry! We’re here to provide assignment help! Our workingment experts provide AI-free, 100% plagiarism-free solutions according to your needs. With years of experience and over 5,000 students helped, we specialize in assisting with report writing, presentations, and computer science assignments. Get free samples, detailed AI reports, and reliable guidance. Let our UK-based experts support you—pay for professional assistance and ace your course today!
Hire Assignment Helper Today!
Let's Book Your Work with Our Expert and Get High-Quality Content
