| Category | Assignment | Subject | Education |
|---|---|---|---|
| University | __________ | Module Title | D/618/5218 Network Threats and Vulnerabilities |
| Word Count | 3000 (±10%) |
|---|---|
| Assessment Type | Report |

You are a cybersecurity consultant hired by a mid-sized e-commerce organisation that has recently experienced several network security incidents, including phishing attacks and a suspected data breach. The management is concerned about the vulnerabilities within their network infrastructure and has requested a thorough assessment of their current security measures. Your objective is to evaluate the existing network security practices, identify potential threats, and propose actionable improvements.
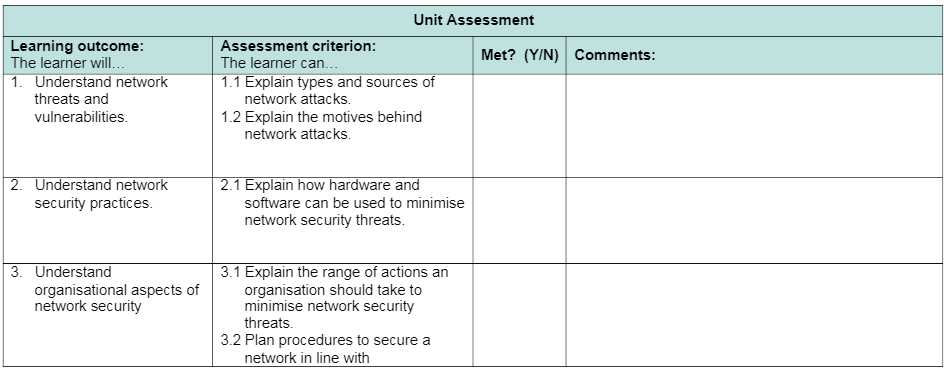
1.1 Explain types and sources of network attacks [AC 1.1]
1.2 Explain the motives behind network attacks [AC 1.2]
2.1 Explain how hardware and software can be used to minimise network security threats [AC 2.1]
2.2 Evaluate email and wireless security features (General Analysis)
Are You Looking The Solution of D/618/5218 Assignment
Order Non Plagiarized Assignment3.1 Explain the range of actions an organisation should take to minimise network security threats [AC 3.1]
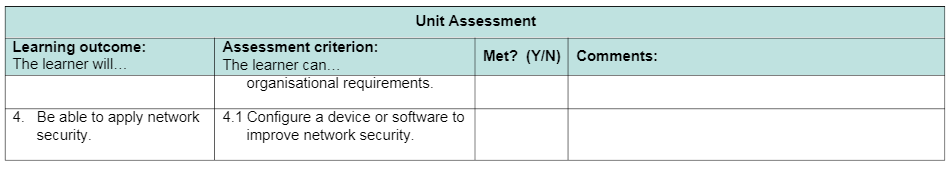
3.2 Plan procedures to secure a network in line with organisational requirements [AC 3.2]
4.1 Configure a device or software to improve network security [AC 4.1]
oSpecific settings and protocols to be implemented (e.g., enabling a firewall, setting up VPN).
oHow these configurations help mitigate the risks identified earlier.
oMethods to assess functionality (e.g., conducting penetration tests, monitoring for anomalies).
oEvaluating performance impacts (e.g., system responsiveness before and after security measures are applied).
Buy Answer of D/618/5218 Assignment & Raise Your Grades
Pay & Buy Non Plagiarized AssignmentNeed last-minute online assignment help with your D/618/5218 Network Threats and Vulnerabilities Assignment? We’re here for you! Our experienced writers deliver high-quality, AI-free, and plagiarism-free assignments at affordable rates. We know how important your grades are, which is why we guarantee on-time delivery and full academic support. You are assured that our Computer Science Assignment Help will make you productive and help you achieve high grades in your academic year. We’ve got you covered. Check out our free assignment examples and see the quality for yourself. We’re available 24/7 to help you succeed in your academic journey. Contact us now to get expert help and score better—without any stress!
Hire Assignment Helper Today!
Let's Book Your Work with Our Expert and Get High-Quality Content
