| Category | Coursework | Subject | Computer Science |
|---|---|---|---|
| University | De Montfort University | Module Title | CSEC5003 Penetration Test Incident Response |
| Title of the assessment | Penetration Test and Incident Response: Cohorts 1, 2 and 3 |
| This coursework item is | Summative |
Please read all sections of this specification carefully. This specification comprises two clearly separated parts. This coursework is to be an individual piece of work. You may NOT work with a colleague.
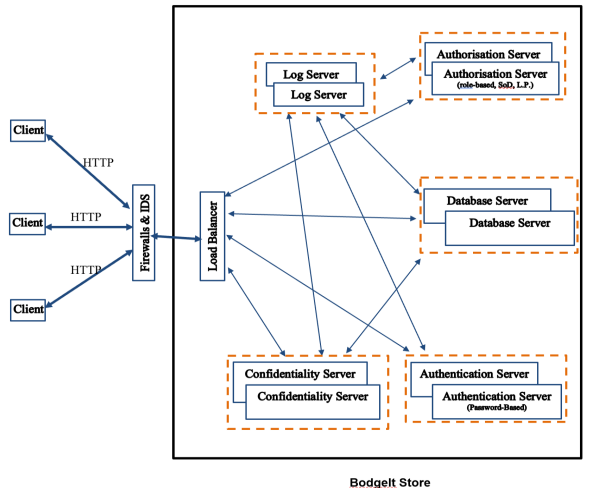
The business manager of a local SME has requested a penetration test to be carried out against their newly developed web application, The Bodgelt Store.
Requirements
This assessment focuses on your ability to report your findings after completing a penetration test:
Do You Need CSEC5003 Assignment of This Question
Order Non-Plagiarized AssignmentScope
The scope of the penetration test is limited to the website using only ports 80 and 443. The Rules of Engagement allow to use any TTP, including existing exploits, and your own bespoke scripts. However, the use of the tool SQLmap is out of scope. Similarly, the implementation of cross-site scripting or Cross-Site Request Forgery is out of scope. Any offline attacks on the victim's Virtual Hard Disk are out of scope. Interacting with the GRUB loader on the coursework VM is out of scope. You should not look at files directly on the coursework VM, and interaction with the target should always occur through the network. Your client has also requested no cross referencing between the Executive Summary, Technical Summary, and Assessment Summary. Each of these documents should address the relevant audience, and be written using the adequate narrative. The technical summary must include a table summarising the vulnerabilities uncovered.
During the pre-engagement meetings, your client has requested using the ATT&CK matrix and risk matrices to describe each vulnerability exploited (attack.mitre.org), supporting the technical summary with an attack flow diagram, and only including recommendations from the MITRE ATT&CK framework.
You will need to download a compressed file (victim_web_app.zip) from the link provided on the Learning Zone shell. You will need VMWare Player to run both VMs, the one containing the web application and the other running Kali Linux.
You need to ascertain the IP address of the victim machine, and then access it with a browser. Point the browser from the test environment at the home page of the website in the VM. This VM contains multiple websites – you need to select The Bodgelt Store from the list.
Scope
Based on the findings of your penetration test, your client is now well aware of the cyber security risk posed to their operation and are thinking about setting up its own Security Operations Centre, but is unsure whether or to commit the resources required. You have been asked to provide advice on the matter and to present a business case to support your advice. You are required to provide:
Buy Answer of This CSEC5003 Assignment & Raise Your Grades
Request to Buy AnswerWhen completed you are required to submit your coursework via:
If you need any support or advice on completing this coursework please visit the Student Matters tab on the CEM Blackboard shell.
The learning outcomes that are assessed by this coursework are:
Get expert coursework help for CSEC5003 Penetration Test Incident Response from our professional team! We specialize in offering high-quality assignment help in the UK, with an option for students to pay our experts to take on their coursework challenges. Need a reference? We also provide a free list of assignment example samples to help you get started. With years of experience, our writers deliver 100% plagiarism-free content and offer unlimited revisions to meet your needs. Trust us to help you excel in your studies!
Hire Assignment Helper Today!
Let's Book Your Work with Our Expert and Get High-Quality Content
