| Category | Assignment | Subject | Computer Science |
|---|---|---|---|
| University | University of West London | Module Title | CP70045E M.Sc. Fundamentals of Cybersecurity |
Context: Read Task 1 from the RSA Lab document.
Follow the instructions provided to generate an RSA key pair. The bn_sample.c program demonstrates how to use OpenSSL's BIGNUM operations for mathematical computations. Using these OpenSSL functions, write a C program that fully implements RSA key generation.
A. Background (Max word count 300): Summarize the background of RSA encryption, including
B. Write a C program named task1.c that performs the following:
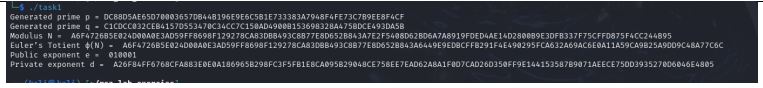
o Generated primes (p, q)
o Modulus (N)
o Euler’s Totient (ϕ(N))
o Public exponent (e)
o Private exponent (d)
o Private exponent (d)
The output should be in this format
Context:
In Question 1, you generated an RSA key pair (N, e, d). Now, in Task 2, you will use the generated key values to first encrypt and then decrypt your “Group Name”
Required:
A. Find a unique group name for yourself, such as group_1, group_2, etc.
B. Write a C program named task2.c that takes plain text input, your group name, performs the following steps:
Step 1: Read public key from keys.txt file Read RSA Modulus (N) in hex format.
Read Public Exponent (e) in hex format. Read Private Exponent (d) in hex format.
Step 2: Convert Message to a BIGNUM
Convert the ASCII input message into a hexadecimal string. Convert the hex string into a BIGNUM.
Step 3: Encrypt the Message
Compute the ciphertext (C) using the RSA encryption formula: C=Me mod N
Print the ciphertext in hexadecimal format.
Step 4: Decrypt the Ciphertext
Compute the decrypted message (M) using the RSA decryption formula: M=Cd mod N
Print the decrypted message in hexadecimal format.
Step 5: Convert Decrypted Hex Back to ASCII
Convert the hexadecimal decrypted message back to ASCII.
Print the final decrypted message and verify that it matches the original input.
Deliverables:
The output should look like below
![]()
Buy Answer of This Assignment & Raise Your Grades
Order Non Plagiarized AssignmentContext: In Q2 (previous task), you implemented RSA encryption and decryption. Now, in Q3, you will extend RSA to digital signatures, using the same key pair (e, d, N) from Q1.
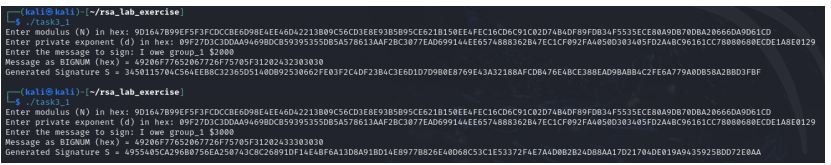
Write a C program named task3.c that takes a message (Your message would be “I owe group_name $2000”) to sign and performs the following steps:
Step 1: Read Inputs
a. Read RSA Modulus (N) in hex format.
b. Read Private Exponent (d) in hex format.
Step 2: Convert the Message to a BIGNUM
Step 3: Generate the RSA Signature
Step 4: Modify the Message and Sign Again
The resulting screenshot should look like below.
Context: In Q3, you implemented RSA signing using the private key (d, N).
Now, in Q4, you will implement RSA signature verification using the public key (e, N). This ensures that the message came from a valid signer and was not modified.
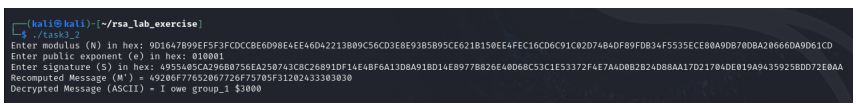
Develop task4.c (Signature Verification Program) which does the following.
Step 1: Read Inputs
Step 2: Verify the Signature
Step 3: Modify the Signature and Re-Verify
Deliverables:
The output should look like below.
In this question you will analyze an encrypted message without knowing the encryption algorithm used. You will be provided with the following files:
A. Decrypt the Ciphertext:
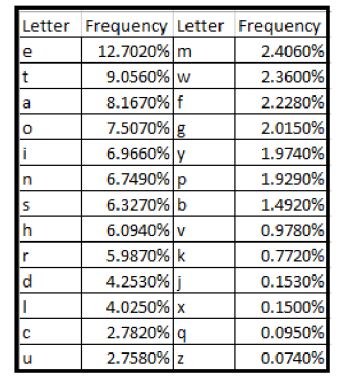
In this part you will create the content for the mappings.txt file. For that first run task5_1.c to perform frequency analysis on ciphertext.txt. This will generate frequency statistics for each letter, helping to determine the most probable letter mappings. Create mappings.txt based on the frequency analysis output. Compare the letter frequencies with typical English letter frequencies to infer the correct substitutions.
When you have the mappings.txt ready. run task5_2.c to decrypt the message using the mappings from mappings.txt. This will output the decrypted text. You can adjust mapping.txt file until you are happy with the result.
B. Reflection and Analysis (Max 250 words)
Buy Non Plagiarized & Properly Structured Assignment Solution
Order Non-Plagiarized AssignmentAre you worried about the CP70045E M.Sc. Fundamentals of Cybersecurity Assignment 01? There's no need to worry! If you need help on assignments, we are here to assist you We also provide free assignment samples of high-quality, original content written by our PhD expert writers, so you can get an idea of the quality. Our focus is to provide you with computer science assignment help in the UK, that too before the deadline! Now stop worrying about late submissions and contact us for the best grades. Hand over your assignment worries to our experts today!
Hire Assignment Helper Today!
Let's Book Your Work with Our Expert and Get High-Quality Content
