| Category | Assignment | Subject | Education |
|---|---|---|---|
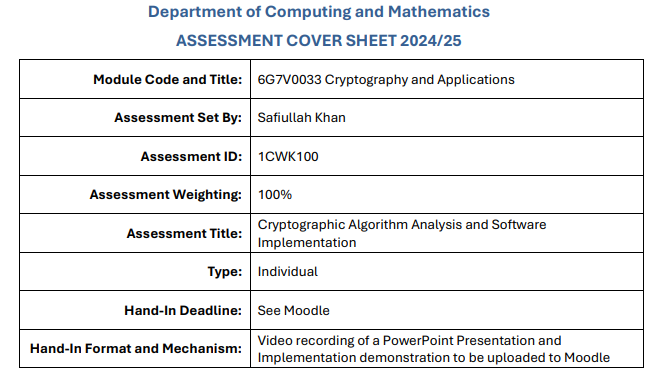
| University | Manchester Metropolitan University (MMU) | Module Title | 6G7V0033 Cryptography and Applications |
LO1 Explain the mathematical computations underpinning cryptographic algorithms.
LO2 Critically analyse basic cryptographic algorithms and propose appropriate uses for them. LO3 Explain use of cryptography in authentication protocols and other emerging applications. LO4 Code and modify algorithms to perform specific encryption/cryptographic tasks.
LO5 Apply a wide range of transferable skills and attributes applicable to industry and research.
Note: it is your responsibility to make sure that your work is complete and available for marking by the deadline. Make sure that you have followed the submission instructions carefully, and your work is submitted in the correct format, using the correct hand-in mechanism (e.g., Moodle upload). If submitting via Moodle, you are advised to check your work after upload, to make sure it has uploaded properly. If submitting via OneDrive, ensure that your tutors have access to the work. Do not alter your work after the deadline. You should make at least one full backup copy of your work.
The timeliness of submissions is strictly monitored and enforced.
All coursework has a late submission window of 7 calendar days, but any work submitted within the late window will be capped at 50%, unless you have an agreed extension. Work submitted after the 7-day late window will be capped at zero unless you have an agreed extension. See ‘Assessment Mitigation’ below for further information on extensions.
Please note that individual tutors are unable to grant any extensions to assessments.
If there is a valid reason why you are unable to submit your assessment by the deadline you may apply for Assessment Mitigation. There are two types of mitigation you can apply for via the module area on Moodle (in the ‘Assessments’ block on the right-hand side of the page):
Further information about Assessment Mitigation is available on the dedicated Assessments page.
Permitted – with changes
The use of generative AI is permitted in this assessment, but please make sure you follow these specific instructions:
We recommend working to the two main principles:
1.Your work should always authentically represent your capabilities.
2.You should never trust the outputs of Generative AI uncritically. Specifically, when it comes to this assessment:
For Task 1 (Algorithm Description and Applications)
For Task 2 (Cryptographic Implementation)
For Task 3 (Video Presentation)
For Task 1 (Algorithm Description and Applications)
For Task 2 (Cryptographic Implementation)
For Task 3 (Video Presentation)
For any other uses of generative AI, you should also follow the instructions in the ‘Are you allowed to use AI in assessments?’ section of the AI Literacy Rise Study Pack or speak to your tutor. All submitted work must be your own original content.
If you are unable to upload your work to Moodle
If you have problems submitting your work through Moodle, you can send your work to the Assessment Management Team using the Contingency Submission Form. Assessment Management will then forward your work to the appropriate person for marking. If you use this submission method, your work must be sent before the published deadline, or it will be logged as a late submission. Alternatively, you can save your work into a single zip folder then upload the zip folder to your university OneDrive and submit a Word document to Moodle which includes a link to the folder. It is your responsibility to make sure you share the OneDrive folder with the Module Leader, or it will not be possible to mark your work.
For further information see the Postgraduate Assessment Regulations on the Assessments and Results information pages
The assignment consists of the following tasks.
The first task is related to exploring the theoretical aspects of modern cryptographic algorithms. You will need to understand the mathematical underpinning of the algorithms and the considerations that influenced their designs.
You must choose a cryptographic algorithm from several possible topics. You will then need to explain the inner workings of the algorithm.
Note: You can choose your algorithm from one of two categories:
1.Simple (algorithms covered completely in the module)
2.Complex (algorithms briefly/not covered in the module)
A choice from the Simple category will limit the possible marks available for the report, as indicated in the marking scheme below.
Provide specific scenarios in which your chosen algorithm can be used. Support your use-case with existing uses in real-world applications where possible, for example including authentication protocols and other emerging applications.
For this task, you will be exploring solutions to the problem of secure storage of data. You will need to implement data encryption along with a suitable key management (secure way to share key) architecture in software. The task is to produce the encrypted backup of files and folders. At the very minimum, the implementation must be able to encrypt/decrypt files using separate keys for two different users.
Note: You can use any algorithm of your choice, it’s not mandatory to use the same algorithm as in Task 1. You are required to include suitable comments in the code.
Further marks will be awarded based on how well the submitted implementation expands on this single requirement. Possible extensions include:
Stuck Your 6G7V0033 Assignment ? Deadlines Are Near?
Hire Assignment Helper Now!You must record a 10–15-minute video. In this video, apart from the explanations of Task 1 and Task 2, you must:
For the submission of Task 1 and Task 2, the following instructions must be considered.
The teaching team is available to support your work on this assignment. Support can be obtained in the timetabled lab sessions. Outside of timetabled lab sessions, you can also contact the teaching team for additional support (contact details are available on the module Moodle page).
Formative feedback will be provided verbally during the assignment support labs. This formative feedback will help you to prepare your own version of these tasks for the summative assignment. Individual summative feedback (incl. the marks) will be uploaded via a comments/marking sheet on Moodle. General feedback given to all students on Moodle.
|
|
Poor |
Acceptable |
Good |
Very Good |
Excellent |
|
Criteria |
0-49% |
50-59% |
60-69% |
70-79% |
80-100% |
|
For Task 1 only: A choice of a complex algorithm has no restriction on marks. |
|||||
|
For Task 1 only: A choice of a simple algorithm will be restricted to marks in the range Poor to Very Good |
|
||||
|
Algorithm |
The algorithm |
The general function |
A straightforward |
The algorithm |
The algorithm |
|
Description and |
presentation was |
of the algorithm was |
presentation of a |
selected was simple. |
selected was |
|
Applications [40 |
unclear and/or |
presented but with |
cryptographic algorithm |
The internal |
complex, taken from |
|
marks] |
incomplete. |
missing/incorrect |
with some brief internal |
operations are |
the latest research in |
|
|
Applications of |
details. Practical use |
operations. A |
thoroughly |
the literature. The |
|
|
algorithm are missing |
of the algorithm is |
reasonable use of the |
presented. A |
internal operations |
|
|
or incoherent. AI is |
presented in a |
algorithm was |
detailed use-case |
are thoroughly |
|
|
used to generate the |
general/vague |
presented. |
was provided that |
presented. A |
|
|
entire description of |
manner without |
|
highlights the |
detailed use-case |
|
|
the cryptographic |
much context. |
|
purpose and |
was provided that |
|
|
algorithm and |
|
|
benefits of the |
highlights the |
|
|
applications. |
|
|
algorithm. The |
purpose and benefits |
|
|
|
|
|
presentation was |
of the algorithm. The |
|
|
|
|
|
complete and |
presentation was |
|
|
|
|
|
accurate. |
complete and accurate. |
|
Cryptographic Implementation [40 marks] |
Implementation is missing or not working. AI- generated code without significant modification is submitted. |
The presentation for implementation is incomplete. Mandatory features are only partially complete. No additional features are discussed. Comments in code were insufficient/not original. |
Implementation performs the basic requirement with some small additional features/capabilities beyond the mandatory ones. The code was organised suitably with generally good comments. |
Implementation is functionally complete with numerous capabilities and features beyond the basic ones. Comments were provided throughout that clearly explained the code. All sources were attributed. |
Original and innovative implementation that satisfies the requirements using several complex and appropriate cryptographic algorithms and techniques. Code is made available in a public repository (e.g., GitHub). |
|
Video Presentation [20 marks] |
The video presentation points are completely/ almost ignored. AI is used to generate the entire script. AI- generated voices or avatars are used. |
The video presentation has some issues with quality, audio clarity, time management, engagement, or explanation clarity, affecting the overall effectiveness and professionalism. |
The video presentation meets the basic requirements for video quality, audio clarity, time management, engagement, and explanation clarity. |
The video presentation is competent, with reasonable quality, clear audio, appropriate time management, decent engagement, and clear explanations. |
The video presentation excels in video quality, audio clarity, time management, engagement, and explanation clarity. It effectively communicates the content and maintains viewer interest, providing a professional and informative experience. |
Buy Answer of 6G7V0033 Assignment & Raise Your Grades
Order Non Plagiarized AssignmentIf you are worried about the 6G7V0033 Cryptography and Applications Assignment? then no need to worry anymore! Our experts provide management assignment help that has been designed for the students. You will get expert guidance and help on assignments that will strengthen your concepts. We also provide you with free assignment samples that will help you understand. And the best part? All the content is 100% original, written by PhD expert writers, and well-researched, so that you get the best quality. So don’t delay now; boost your grades with our help!
Hire Assignment Helper Today!
Let's Book Your Work with Our Expert and Get High-Quality Content
