| Category | Assignment | Subject | Management |
|---|---|---|---|
| University | The University of Law | Module Title | Business Simulation Cyber Security |
| Word Count | 2,500 words |
|---|---|
| Assessment Type | Individual Portfolio |
| Academic Year | 2024-25 |
1. Critically analyse the business environment to categorise the determinants of business performance.
2. Examine business situations to establish the organisation's capabilities; identify critical issues and evaluate options available to address the issues.
3. Develop an understanding of how to approach management decision-making, assessing alternatives, and making deliberate, thoughtful decisions.
4. Justify the decisions made on the allocation of resources and evidence the value added clearly.
5. Appraise Environmental, Social, and Governance (ESG) considerations and practices and the implications for the organisation's perception and performance.
Assessment details: Individual Portfolio, 100% (equivalent to 2,500 words)
A portfolio organised to collect evidence of your learning journey will be used to assess this module. The portfolio will showcase the knowledge gained, skills developed, and decision-making experience gained throughout the simulation exercise.
You are a junior cybersecurity analyst hired by a fictional client, "VulnTech Inc.". The company has deployed a server (Check Assessment Information) for their legacy systems. There are five standard phases of ethical hacking.
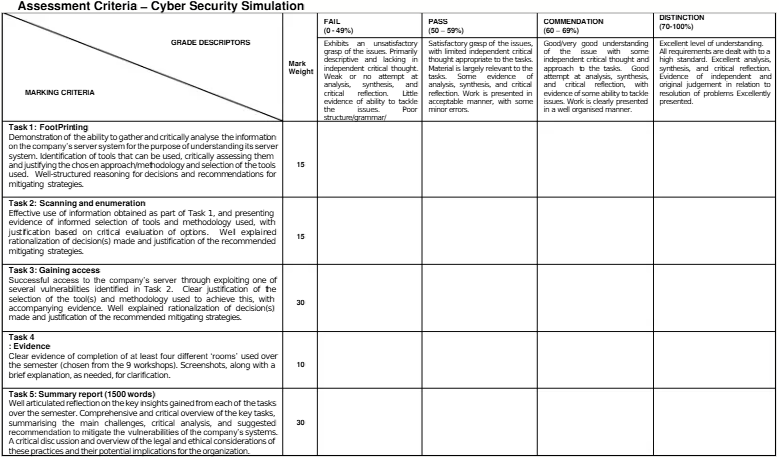
1. FootPrinting
2. Scanning and enumeration
3. Gaining access
4. Maintaining access
5. Post-exploitation
As a junior analyst, "VulnTech Inc." asked you to perform only the first 3 phases, and the senior cybersecurity analyst will handle the rest of the phases. Your task is to find out vulnerabilities and hack into this system, document your findings, and recommend mitigation strategies.
You will gather information on the VulnTech server system to understand the company better and its server system. Present evidence of the tools utilised and justify your selection, critically evaluating the chosen methodology. Additionally, explain the reasoning behind your decisions and recommend mitigation strategies.
You will scan and enumerate VulnTech's server system to identify potential vulnerabilities using the information you gathered in Task 1. Present evidence of the tools utilised and justify your selection, critically evaluating the chosen methodology. Additionally, explain the reasoning behind your decisions and recommend mitigation strategies.
You will access VulnTech's server by exploiting one of the multiple vulnerabilities you identified in Task 2. Present evidence of the tools utilised and justify your selection, critically evaluating the chosen methodology. Additionally, explain the reasoning behind your decisions and recommend mitigation strategies.
Provide evidence (screenshot) of completion of at least four different modules/rooms you used over the semester (9 workshops).
After completing the tasks, you must prepare a summary report. This report allows you to articulate and reflect on the key insights gained from each task. It serves as an opportunity to consolidate your learning, offering a comprehensive overview of the knowledge and understanding acquired throughout the process. Additionally, you should address the legal and ethical considerations of these practices and their potential implications for the organisation.
Do You Need an Assignment for This Question
Order Non-Plagiarised AssignmentYour portfolio should consist of five pages in PebblePad, each corresponding to the assigned tasks.
Any write-up in the Portfolio should be written in font size 11, single spacing in PebblePad.
Proper citations are essential. All tasks require referencing academic and other sources, listed in a Harvard Referencing style, present a reference list at the end of the Portfolio. Whenever you use external sources (pictures, tables, definitions, line of argumentation), clearly state this at the end of the sentence or paragraph by providing a reference to the original article using the Harvard Referencing style.
Please refer to the marking criteria (below) for a breakdown of how this assignment will be marked.
Do you need help with an assignment for Business Simulation Cyber Security? Look no further! We are here for management assignment help. We also provide free assignment solutions written by PhD expert writers—100% original content, no plagiarism! Plus, we also provide assignment help, that too by completing it before the deadline. Quality and accuracy are taken care of completely. So contact us today and be stress-free!
Hire Assignment Helper Today!
Let's Book Your Work with Our Expert and Get High-Quality Content
