What is Doctoral Dissertation?
A doctoral dissertation is one of the longest pieces of writing, in which you are the author, and you need to provide a ...

In today's era, our dependence on digital technology is increasing. For which there is a greater need to protect personal data from any cybercrime. Whenever we visit any site, we mostly have to enter our details, which remain secret with every company. Nowadays, many students are showing their interest in the Cyber Security course.
As many of you must have done, if you are here, you must be pursuing your degree in cybersecurity or any related field. Being students of any subject, there is one thing that every student has to face once in their academic journey, and that is a Dissertation. One of the first things that you have to deal with in a dissertation is finding the right topic.
Our experts who are professional dissertation helpers have been handling so many dissertation for so many years, have taken care of your first issue, as here you will find 300+ topics related to cyber security dissertation. They say that students should always choose a topic that interests them. This is the reason we have shared topics from different fields including data security, honeypot, privacy, cyber threats, cloud security and many more.
To help you out with other issues of dissertation our experts have also provided some other information which will make it easy for you to write a dissertation. They have mentioned a brief explanation of cyber security and its type so that you can get an understanding of what you are actually writing for. We have also mentioned a complete process of how you can find a perfect topic for yourself. So, go on then and find and be free of stress of selecting the right dissertation topics.
The basic process of providing safety to networks, mobile devices, electronic systems, servers, and data from various malicious intrusions is considered Cybersecurity. It is also considered the security of electronic information and the security of technology. Nowadays, students are showing a lot of interest in cyber cybersecurity topic dissertation.
There are several basic areas into which the phrase "cybersecurity" can be subdivided and is used in a range of contexts, including business and mobile computing.
The procedure that involves protecting computer networks from different trespassers, whether they be malicious software or they be malevolent actors, all comes under network security.
Note: Cybersecurity requires the collection of data, so make sure you focus more on research and learn how to write a research question for a dissertation, as it will make it easy for you to know what to research.
So, it’s important that we also take care of the security thing. Below, you will get the information about how many network security threats there are:
1. Network Security: This kind of security focuses on saving the data and network transfers in multiple web pages, and it tries to secure a safe web network for you.
2. Information Security: It focuses on saving data from unknown access, be it through a network or any URL link, safeguarding any sensitive information.
3. Endpoint Security: In this particular security, it involves protecting devices and other gadgets from cyber threats. Computers, laptops, tablets and mobile phones are secured with the help of anti-virus software.
We are sure that you must have an overview of the, now you have understood an overview and understand the categories of cybersecurity. Now, let's move ahead to the next section, which is for the students who are struggling to find dissertation topics for cybersecurity. We have provided you with enough amount of dissertation ideas for you to you can select any kind of cybersecurity topic for your Computer Science Dissertation Topics.
Here are all your disstertaion topics that you can select according to your preference. All of these topics have good research material available and also they have been in trends in recent years. So you do not need to be worried about anything else. You just have to select a topic that makes you feel, "I want to learn more about it". Selecting a interested topic will make writing a dissertation process less boring and complicated for you. In today's honeypot is the field that is trending as many students are getting registered in this. Knowing we can not make the mistake of not adding honeypot cybersecurity dissertation topics 2024 2025. We have mentioned unique topics from both the years, so get the one you prefer.
|
1. Analysing Cybersecurity Techniques for Safeguarding Important National Assets |
|
2. Examining the Impact of Cybersecurity Laws and Legal Structures |
|
3. Examining the Application of Fraud Technologies in Cyber Defence Tactics |
|
4. Evaluating the safety Consequences of Upcoming Technologies, including Quantum Internet and Neuromorphic Technology. |
|
5. Exploring Cybersecurity Risks Related to the Airline and Aerospace Sector |
|
6. Looking into the Importance of Cybersecurity in Maintaining Election Transparency and Protecting Polling Machines |
|
7. What is a DDOS attack? And how does it impact different devices? |
|
8. Addressing the Security Issues of AI and Machine Learning Systems in Cyber Crime |
|
9. Analysing Cybersecurity Threats and Approaches in the Media and Television Sector |
|
10. The study of the Privacy and Security Risks of Self-Driving Cars and Linked Car Technology |
Miscellaneous |
| 1. Monitoring Cybersecurity Concerns and Options in the Video and Gaming Business |
| 2. Studying the Contribution of Cybersecurity in Safeguarding Critical Services from Digital Warfare Strikes |
| 3. Assessing Cybersecurity Barriers in the Defence and Army Sector |
| 4. Questioning the Effects of Cybersecurity on the Use of Digital Forensics and Response to Incident Standards |
| 5. Evaluating the Privacy Issues of Quantum Cryptography for Upcoming Cyber |
|
6. Reviewing the Effects of Cybersecurity in Maintaining Data Security and Validity in Open Blockchain Systems |
Note: Make sure if you are looking these dissertation topics for your MBA, then you must get an understanding of how you can find dissertation topics for MBA, as when you are looking for topic for degree like MBA you cannot just go with whatever you found. You must select a topic that is going to have an impact on future research as well.
| 1. Data privacy and its implications for cybersecurity |
| 2. Cybersecurity effects of remote working on an organisation. |
| 3. The importance of communications and network cybersecurity |
| 4. Security measures to be taken Once A cybersecurity breach has occurred. |
| 5. Cyber security in managing money laundering: the importance. |
| 6. Effect of law on cyber crimes |
| 7. Benefits of penetration testing against cyber attacks: critical review. |
| 8. The effects of malware in the context of the cybersecurity of an organisation. |
| 9. Need to install anti-malware applications to minimise attacks by hackers. |
| 10. Cybersecurity and cookies: how the two are related. |
In case you are wondering why to focus so much on selecting a topic, you must understand the importance of choosing the right dissertation topic.
Data security for the baking sector
How weak passwords could be the reason for financial cyber robbery
Manipulating social media accounts
Restrictions on data security
International affairs in the cybersecurity world
Cyber attacks by web robots
The negative and positive influences of cryptocurrency
Data privacy in the Healthcare department
How the data security world incorporates
Evolution of Coded Messages
Significance of malware attacks in the IT world
Lack of wireless information transmission
How to maintain digital privacy in today’s advanced times
Inefficient VPN functionality
Robbery of an organisation’s data
Breaching risk in the banking sector
Intervention of cyber criminals in personal data
Significance of data backup
Positive usage of cybersecurity in the software world
Cases of Data Breaching of 2023
Safe computing and increased cases of cybercrime
Ways of being safe from cybercrime
What is data breaching
How to know the difference between viruses and antivirus software in detail
Increased cases of mobile scams and cybercrime.
How to keep the removable media like USB & CD.
Extra precautions and safety tools to keep the accounts safe and secure
How security breaches can affect companies
Why not use public WiFi, and how does it impact on person’s privacy
Cloud safety of data and storage
Cruciality of website traffic and banners in cybersecurity
Always check and keep a distance from the network area access.
What is a zero-day attack, and what is its impact?
Technology in 7/11
What is a signature network
Understand the IP address default
Advancements in techniques like end-to-end encryption
Multiple benefits of network security and tests
Understand the SQL attack
Risky data and its possible effects from both good and bad perspectives
Operational vulnerability in cybersecurity
Adequate use of AI
These are some of the best honeypot cyberssecurity dissertation topics. These topics have gain popularity in 2025, as recently many students and researches have been seen writing dissertation and doing research on these topics.
What are the elements of the authentication process of banking
How can cyber-bullying increase the cases of suicide and mental health
Blockchain attacks and their prevention
Cryptocurrency
Attack of XSS on different applications
How to remove malware from your application
How to build a strong firewall to secure your data from hacking
What is cyber harassment, and how can to save oneself from this cyber harassment
What is cyberterrorism
How the USA regulate their cybercrime
Analysing the benefits of blockchain technology in improving and elevating cybersecurity problems and the prevention of malware.
How MLA intervenes in searching systems
Decoding the framework of cybersecurity: stepping into the security indications of the Internet of Things (IoT)
Ethical hacking: Analyse the usage of discovering and decreasing threats to cybersecurity
Operating systems’ actions and the reliability of securing them against the attacks of cybercriminals.
The repercussions of the computer forensic field, along with its significant importance in the advanced age.
The effect of the bug evaluation and minimised data breaches and their benefits
Difference between the Asymmetric, Cyber and Hybrid Threats.
Analyse the motive of cybersecurity awareness and training in handling insider threats.
Psychological factors impacting the awareness of cybersecurity
How helpful is Gamification for cybersecurity training
What is the impact of cybersecurity policies on employee behaviour
User point of view for the new two-factor authentication security in their applications
Problems of cybersecurity in remote work environments
Social media and its function in the cyberattack problems
Cybersecurity awareness among the MSMEs
Estimating the importance of cybersecurity attention programs
Learning the behaviour of hackers and cybercriminals
Errors made by human contributors in cybersecurity breaches
These are the topics which can be considered best Honeypot Dissertation Topics Msc Cybersecurity for year 2024. You can go with these topics if you find your interested among these topics. You do not have worry about are they up to date or not, selecting a topic from last year is more beneficial as you will have more research material available.
The transition of cyber extortion attacks and countermeasures
Risk of the cyber management model in the finance sector
Known dangers and mitigation techniques
Evaluating the importance of cyber insurance
The effect of cybersecurity violations on stock market performance
Social engineering attacks and prevention methods
Phishing attack tendencies and relief methods
Cyber risk in enterprise networks
No Trust Architecture and Its Significance
The function of honeypots in the research of cybersecurity
Security-related problems in multi-cloud settings
Data privacy: Challenges and solutions
Cloud-based violation detection systems
Comparative estimation of cloud encryption practices
Safe cloud storage for data integrity verification
The effect of quantum computing on cloud security
Cloud forensics: problems and best methods
Security implications of serverless computing
Obedience problems in cloud-based security management
AI-based cloud security mechanisation
Introduction to Cybersecurity
Importance of Cyber Hygiene
Common Cyber Criticalities and How to Dodge Them
Difference Between Cybersecurity and Information Security
Cybersecurity for Newbies: Important Tips
Different Types of Phishing Attacks and How to Control Them
Define Social Engineering
Explain Man-in-the-Middle Attacks (MITM)
Distributed Denial-of-Service (DDoS) Attacks
Viruses and Malware Types and How They Work
What are Zero-Day Exploits: Why They Are Dangerous
Known Threats in Cybersecurity
What are the significant uses of Strong Passwords in banking-related Applications
Learn How to Use Password Management Safely
Double and Multi-Factor Authentication Explained
How Biometric Security Works: Pros and Cons
Common Password Mistakes People Make
The Role of End-to-end Encryption in Cybersecurity
How to Protect Important and Personal Data Online
Cybersecurity for Social Media users and usage
Why Public Wi-Fi and How to Stay Safe
Privacy Settings: How to Secure Your Online Accounts
Introduction to Firewalls and How They Work
What is a VPN and Why Should You Use One?
Cloud Security: Protecting Data in the Cloud
The Importance of Secure Wi-Fi Networks
Network Security Best Practices
How AI is Used in Cybersecurity
The Role of Blockchain in Cybersecurity
Cybersecurity Risks in IoT (Internet of Things)
Protecting Smart Home Devices from Hackers
The Future of Quantum Computing and Cybersecurity
Introduction to Cyber Laws and Regulations
GDPR and How It Affects Online Privacy
Ethical Hacking vs. Black Hat Hacking
What is a Bug Bounty Program?
The Role of Cybersecurity in Digital Forensics
Cybersecurity Usage in Healthcare: Protecting Patient Data
Cyber Threats in Financial Services
The Importance of Cybersecurity in Small Businesses
Cybersecurity for Remote Workers
Online Safety Tips for Kids and Teens
Is there a safe Career in Cybersecurity?
What are the top Cybersecurity Certifications for beginners?
Why Cybersecurity is in High Demand
Define How to Become an Ethical Hacker
What are the chances and future of Cybersecurity jobs
Impact of social media: how it changed the world?
The changes social media has made in communication
Which effect is more negative or positive of social media
How is social media helping positively in society?
Can social media impact political leanings?
Studying the use of social media during the COVID-19 pandemic? Awareness vs. Misinformation
Has social media made the government more accountable towards the locals?
Role of social media in promoting gender equality
How is Social Media and Mental Health related when we see today’s generation?
How does trending syndrome affect self-esteem?
Why is validation on social media so important for the young generation?
Does social media create a false sense of fame?
Why are social media and suicide being linked increasingly?
Social media helped in reducing the stigma attached to depression.
How did social media provide mental support to people stuck alone during the lockdown?
How does cyberbullying impact the confidence of young people?
Social media can induce an inferiority complex among people.
Build an online enterprise resource planning system.
Maintain confidentiality and privacy in e-health records.
Image Sequences for human detection and recognition
Personal cross-media information management.
Create SMS Marketing Software
Develop an online air ticket reservation system.
Machine learning and Image processing for assistive visual interaction
Develop a traffic parking management and parking lot system
Improve performance, safety, and security in database, information & networking systems
Intelligent power management and monitoring for enterprises and homes
Develop advanced cybersecurity measures to protect IoT Devices.
Create AI Algorithms for Predictive Analytics in E-commerce.
Discuss the role of IoT in Sustainable Smart Cities Development.
Optimise cloud storage security protocols for enterprise data protection.
Real-time data analytics in smart city management.
Blockchain applications in securing healthcare records.
Improve User Experience (UX) Design for Mobile Applications.
Enhance customer shopping experience in retail stores using AR.
Discuss the ethical implications of AI in employment
Develop energy-efficient protocols for mobile ad hoc networks
Analyse consumer data for personalised marketing in e-commerce
Future applications and current limitations of Quantum Computing:
Optimise a 3D Topology Scheme for M2M Communications
Improve DQ access protocol for cellular-based massive M2M communications
Examine the impact of quantum computing on current cryptography methods.
Analyse the impact of agile methodologies on the software development life cycle.
Machine Learning approaches for detecting fake news on social media.
Discuss security challenges in IoT Networks and Possible Countermeasures.
Machine Learning Algorithms for Intrusion Detection Systems.
Analyse the efficiency and challenges of DevOps in Practice:
Analyse the efficiency of Multi-Cloud Environments for Large-scale Data Processing.
Machine Learning Techniques for Big Data Processing in Healthcare.
Implications of Smart Contracts in Blockchain for the Financial Industry.
Virtual Reality (VR) and its effectiveness in educational environments.
Understanding the basics of the protection of vulnerable systems
Importance of AI on Cybersecurity Strategies
Examining the impact of the blockchain on improving the safety of data
Analysing Machine Learning's Potential in Identifying and Avoiding Cyber Attacks
Evaluating the efficacy of biometric authentication methods to improve safety
Evaluating the safety and consequences of 5G networks and future methods of communication
Exploring Cybersecurity Risks in the Banking and Insurance Sector
Understanding the Impact of Cyber Insurance in controlling and minimising cyber hazards
Examining the security hazards associated with working from home and telecommuting
Looking into the Use of Cyber Threat Awareness in Proactive Digital Defence
| 1. Investigating the Legal and Moral Issues of Cybersecurity Response to Incidents |
| 2. Evaluating the Privacy and Safety Risks of Modern Cities and Urban Facilities |
| 3. Evaluating Cybersecurity Guidelines for Small or Medium Enterprises (SMEs) |
| 4. Exploring Cybersecurity Issues in Purchasing and Managing Suppliers |
| 5. Investigating the Importance of Cybersecurity in Safeguarding Virtual Identities and Private Information |
| 6. Evaluating the Safety Risks of Medical Equipment and Healthcare Systems |
| 7. Measuring the detrimental effects of attacks involving social engineering on cybersecurity |
| 8. Researching Cybersecurity Concerns in the Educational Sector |
| 9. Investigating the Impact of Cyber Threat Tracking in Proactive Cyber Defence Systems |
| 10. Considering the Safety Hazards and Advantages of BYOD Regulations |
Cybersecurity is one of the most emerging fields today, which is why students are looking for a cybersecurity dissertation Topic. With everyone and everything on the internet, one big concern that arises is the cybersecurity of all the crucial data of so many people. This is the reason the majority of students are looking towards this field and want to learn more about it.
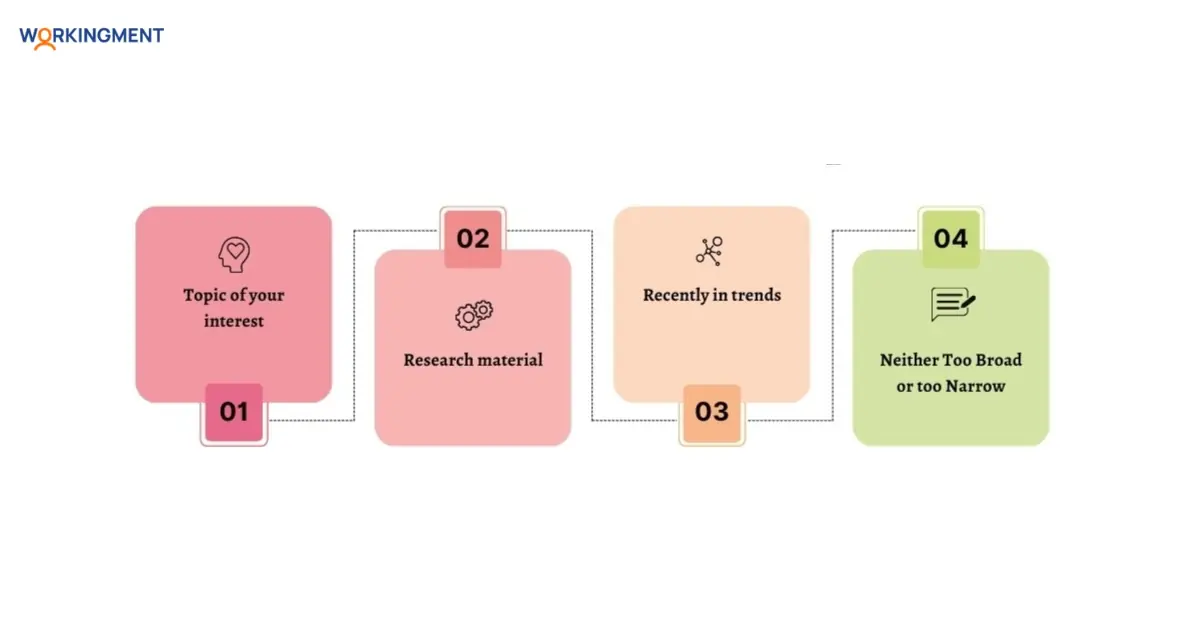
Selecting an accurate dissertation topic is one of the most important factors in getting good grades in your dissertation. So, for such an important thing, we should learn the accurate process of selecting the right topic for your dissertation.
Topic of your interest: The first thing that you need to do is look for the topic that interests you the most, as you must have a topic that you like researching and want to learn more about.
Research material: The next thing that you should look at while selecting the topic is how much material is available for that topic. Do not select any topic that has very limited information available on the internet or anywhere, as this will take a lot of your time. You can get help from good dissertation writing services for this part, as they can guide you by providing information on topics that are easy to research.
Recently in trends: Analyse the popular topic for your dissertation writing. If this is tough for you to find the one for you, then you can get help from a dissertation helper who can help you with the dissertation writing as well as with choosing the right topic. Below are some topics which are most trending and will allow you to take ideas for your cybersecurity dissertation writing
Restrictions on data security
International affairs in the cybersecurity world
Cyber attacks by web robots
The negative and positive influences of cryptocurrency
Data privacy in the Healthcare department
How the data security world incorporates
For more, just scroll down to have the most interesting and trending topics for your cybersecurity dissertation writing.
Neither too broad nor too narrow: Make sure you choose a topic that is neither too broad nor too narrow, as having too broad will confuse you with the large possibility of outcomes and having too narrow will limit your possibility of finding a new result from previously published articles. You can also take expert advice and tips for your dissertation success.
Often, students struggle with their cybersecurity dissertation writing topic. And seek help or assistance from the assessment writing services. You and I both are aware of the importance of good grades when we talk about the students' careers. We have made sure to provide the best and trending topics for your cybersecurity dissertation. Additionally, in this blog, you will find the necessary steps which you should consider while choosing your dissertation writing topic.
At Workingment, you will get all the right from scratch. Our writers can provide you with the topic selection if needed for the final draft of your Cyber Security Dissertation. Along with this make sure that you know how to write each part of the dissertation, as a student you should be aware of how to write a dissertation introduction or other components but just in case you are not aware of these things kindly make yourself informed and familiar with these things as it's important that before writing a student have that ample amount of information so there are no chances of getting rejected your dissertation.
When cybercrime is related to the fraud of any funds or related to someone's bank account. Unethical transfer of funds is one of the most common ones.
The biggest issues in cybersecurity include Insider threats, Third-party exposure, social engineering, Artificial intelligence cyber threats, ransomware, and many others.
Cybersecurity involves various topics including, cloud security, AI security, network security, application security, mobile security, and endpoint security.
Yes, there is no such issue in writing a dissertation for any student who is not pursuing this subject.
Let's Book Your Work with Our Expert and Get High-Quality Content

Loved reading this Blog? Share your valuable thoughts in the comment section.
Add comment