| Category | Assignment | Subject | Computer Science |
|---|---|---|---|
| University | Northumbria University | Module Title | KV6009 Advanced Security |
| Word Count | 2000 Words |
|---|---|
| Assessment Type | Report |
| Assessment Title | Practical Research Report |
| Academic Year | 2024-25 |
The learning outcomes (LOS) for this module are: -
L01 - Understand number systems, mathematical functions, and basics of cryptography.
L02-Design and develop secure networks and systems, incorporating threat modelling and security testing throughout the development lifecycle. Design and develop the cryptographic mechanism for public key infrastructure.
L03 - Practically test and implement encryption and decryption cryptographic functions, methods and protocol security mechanisms and protocols to safeguard the critical infrastructures of organisations.
L04 - Practically apply and validate various cryptographic security protocols and systems by identifying vulnerabilities, performing manual/automated penetration testing, and evaluating results using various tools and methods and perform manual/automated cryptanalysis using logical methods and automated tools.
L05 - Cultivate a curious mindset through independent exploration of emerging cybersecurity trends, technologies, and their potential impact on society. Work as a team to develop a group project identifying equality, diversity and multicultural issues while demonstrating research and enquiry skills.
This assessment addresses learning outcomes LO2, LO3, LO4 and LO5.
XYZ Corporation is a medium-sized organisation that relies heavily on IT services to support its operations. They are in the process of upgrading their infrastructure and need to ensure their services are configured securely to protect against potential threats. You have been hired as IT consultants to assist XYZ Corporation in configuring its services securely. The Company has identified the following areas as priorities:
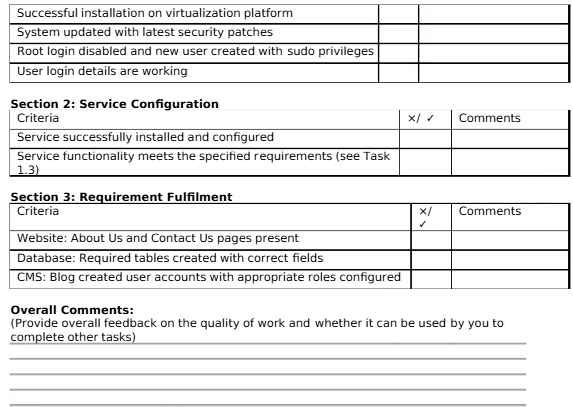
1. Choose a Linux server distribution that is appropriate for the chosen service.
a. Install the chosen Linux server distribution on a selected virtualisation platform (VirtualBox or VMware Workstation Pro)
b. Once the Linux distribution is installed, ensure it is up to date with the latest security patches and updates.
c. Disable root login and create a new user with sudo privileges. The new username must be your name, and the password should be your student number.
d. Demonstrate that you can access the server via SSH using another client instance.
2. Choose one of the service categories below to focus on. For the chosen category, you may choose any of the following corresponding technologies (or choose any other software that you are comfortable working with) and configure it within your Linux server distribution.
a. Web Service: Apache (apache2), Nginx (nginx)
b. Database Service: MySQL (mysql-server), PostgreSQL (postgresql)
c. CMS: WordPress (wordpress), Drupal (drupal)
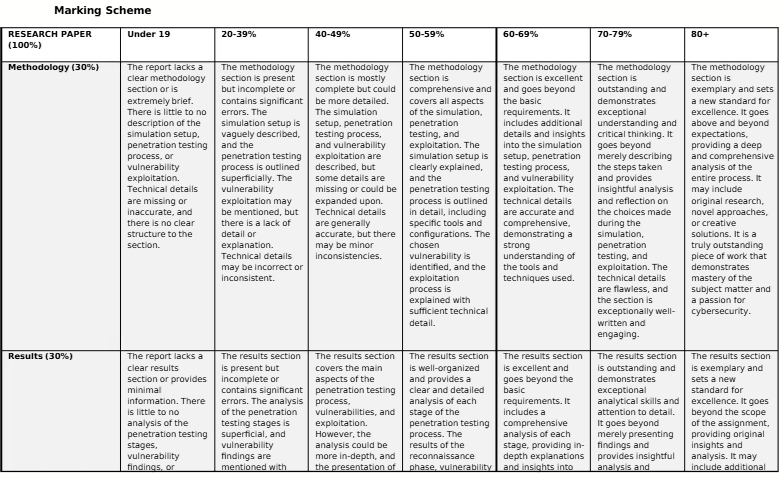
3. Ensure your chosen services follow the given requirements criteria.
a. Website: About Us Page, Contact Us Page (You do not need to worry about populating these pages with content, and you can take the code from other sources)
b. Database: Create an appropriate database/s and add the following tables to that database: Products Table (ID, name, price), Customers Table (ID, name, email, address).
c. CMS: Create a blog (You do not need to worry about populating these pages with content, and you can take the code from other sources), Configure user accounts with appropriate roles (At least two)
4. Use a client machine to show that the service you have configured is working correctly.
a. Use a web browser on the client machine to access the website.
b. Use a database client application (e.g., MySQL Workbench, pgAdmin) on the client machine to connect to the database server.
c. Use a web browser on the client machine to access the CMS admin dashboard.
For this assessment, you will be assigned a classmate, and you must share your final configuration with them. Once you receive the final configuration from the chosen peer, you will then perform Tasks 2 and 3 on their configured server instances.
1. Choose an appropriate methodology (Black box, White box or Grey box) for carrying out penetration testing tasks. Clearly explain in your documentation why you chose this methodology.
2. Information Gathering: Gather information about the target service and OS (open ports, services running, versions).
3. Vulnerability Scanning: Use any vulnerability scanner to scan for known vulnerabilities in the identified service.
4. Attempt to exploit the service or software. Record any successful or unsuccessful exploitation attempt.
5. Provide a threat modelling risk assessment for the VM Instance. Include the following information on the risk assessment: What service you tested, what can go wrong in the given configuration, what can you do to improve the security of the service, and how will you rate the configuration that was given to you.
1. Choose any of the following security measures based on the service your peer has configured.
a. Web Service
b. Database Service
c. Content Management Service
2. Install the iptables and configure the rules according to the following requirements. You do not have to show that the rules are working.
Achieve Higher Grades with KV6009 Assignment Solutions
Order Non-Plagiarised Assignment1. On 31 March 2025, you will share your VM configuration with your peer. No extensions are provided for this submission.
2. On the 7th of April 2025, you will submit a peer evaluation form to Blackboard, which evaluates the instance you received from your peer. No extensions are provided for this submission.
3. Document the server setup, service configuration, penetration testing and security configuration through screen recordings accompanied by a voice-over explanation.
4. Upload the recorded videos with your report on the day of submission.
5. Failure to submit the video or the absence of your audio commentary in the video will result in no marks being awarded for the relevant sections.
6. There's no need to enhance the video with additional effects.
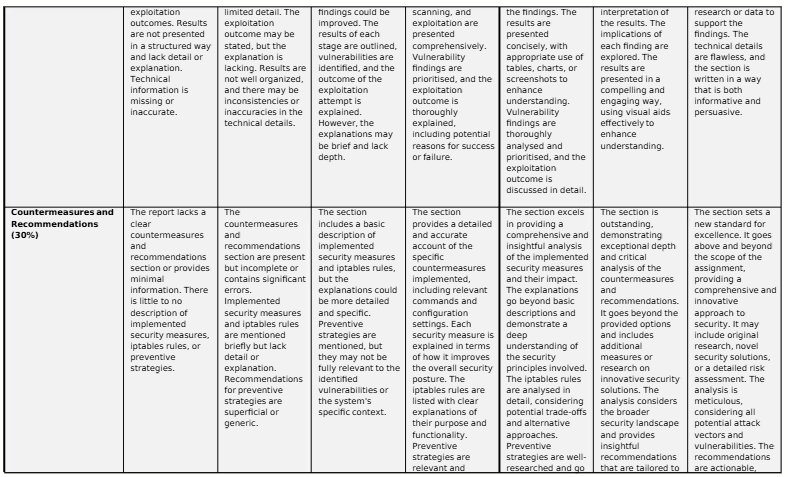
Your final report should be no more than 2000 words. Suggested structure for report:
1. Methodology
a. Simulation Setup: Describe the setup in detail. This includes the server setup and software used, and any other relevant technical specifications.
b. Penetration Testing: Explain how information about the target was collected. State the vulnerability scanner chosen for this task and justify why this scanner was selected. Describe how the scanner was configured.
c. Identify the specific vulnerability chosen for exploitation. Explain the reasoning behind selecting this vulnerability. Specify whether the Metasploit framework or a custom exploit was used. If using Metasploit, mention the module name. If using a custom exploit, briefly describe it. Provide an overview of the steps taken to execute the exploit.
2. Results/Discussion
a. Analysis of penetration testing Stages: Break down the testing into its different stages and present the results for each stage. Briefly explain the results of the reconnaissance phase, highlighting open ports, running services, and their versions.
b. Summarise the vulnerabilities identified by the scanner. Prioritise the vulnerabilities based on their severity or potential impact.
c. Describe the outcome of the exploitation attempt. Was it successful? If so, what level of access was gained? If not, what were the potential reasons?
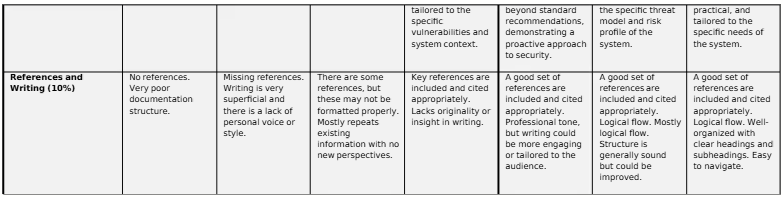
3. Countermeasures/Recommendations
a. Specific Countermeasures configured: Detail each security measure implemented, referencing the options provided (a-d). Provide any relevant commands or configuration settings. Explain how each measure improves the overall security posture of the service.
b. List each iptables rule that was implemented, including the full command syntax and a brief explanation of its purpose.
c. Preventative Strategies: Recommend further strategies to secure the system from attacks in the future.
Your final paper should be no more than 2000 words (excluding references). The marking scheme showing the assessment criteria and mark allocation for both parts is shown at the end of the assignment brief.
General Guidance
The guidance below applies to both parts of the assignment. Please read this guidance carefully.
Hire Experts to solve this assignment Before your Deadline
Buy Today Contact UsAre you trying to find someone who can help with my KV6009 Advanced Security? Well! You're in the right place, our podium, Workingment, provides Computer Science Assignment Help. Our well-researched and talented professors can also provide you with odd assignments. Suppose you're judging whether to Write My Assignment with our professors. No doubt! Our team can help with your assignment. We also provide Free Sample assignments for your guidance. Get in touch right now!
Hire Assignment Helper Today!
Let's Book Your Work with Our Expert and Get High-Quality Content
